Approov Blog
Mobile App Authentication (7)

The Top 6 Mobile API Protection Techniques - Are They Enough?
December 22, 2018
APIs are a necessary and central part of the strategy of any digital business that wants to stay competitive and monetize its assets. Additionally, end users’ form factor of choice when using digital services is now firmly mobile. The trend towards APIs and mobile devices has moved the attack surface in a significant way and digital businesses must adapt and evolve their security policies accordingly. Read Full Story

42Crunch and CriticalBlue Announce Partnership
November 23, 2018
Joint solution to ensure APIs are built correctly and used legitimately. Read Full Story

Approov Cordova QuickStart
June 15, 2018
Editor's note: This post was originally published in June 2018 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in July 2020. Our aim is to make the process of integrating Approov into your mobile app easy. Our Cordova Advanced-HTTP Quickstart allows you to get up and running with Approov easily, whether you are building a new Cordova app that uses Cordova Advanced HTTP or are adapting an existing one to have an improved security posture. Read Full Story

React Native iOS: Bridging an iOS Native Module For App Authentication
May 9, 2018
Photo by Liu Zai Hou on Unsplash Read Full Story

Positive Technologies Partners with CriticalBlue
January 29, 2018
Happy to announce that we are partnering with the great people at Positive Technologies to provide comprehensive protection across both Mobile and Web Channels. See the full press release for details on the API security partners. Read Full Story

Approov in Parallel With User Authentication
January 22, 2018
In my last post in this series, I introduced Approov, the app authentication solution, and described how it tackles the problem of API protection in a novel and proactive way. In this post, I want to focus on the reasons API publishers need app authentication as part of their mobile security defense, and specifically why it should work alongside user authentication. In our discussions with new customers we often find that we need to explain the difference between the two as well as the contributions that each one provides. Read Full Story

A Brief Introduction to Approov
January 19, 2018
An article on wired summarises 25 data breaches that made headlines during 2017. The implication in the article, and the general impression of those who take an interest, is that 2018 will bring more of the same in an ever accelerating trend of discovery and disclosure. The growth in attacks indicates that companies of all sizes should continually raise the defensive bar and Approov raises that bar significantly. In this short post I will provide a high-level view of what Approov does and how it works. Read Full Story

Practical API Security Walkthrough — Part 4
January 18, 2018
Editor's note: This post was originally published in January 2018 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in May 2021. Welcome back! This is the fourth and final part of a mini series which uses a fictional product, “ShipFast”, to walk you through the process of defending against various exploits in a mobile application to gain access to data on a remote server allowing real users of the system to gain an unfair business advantage at the expense of the company. In this post, I'll dive into the third API security attack scenario and what is required to effectively defend against it. Read Full Story
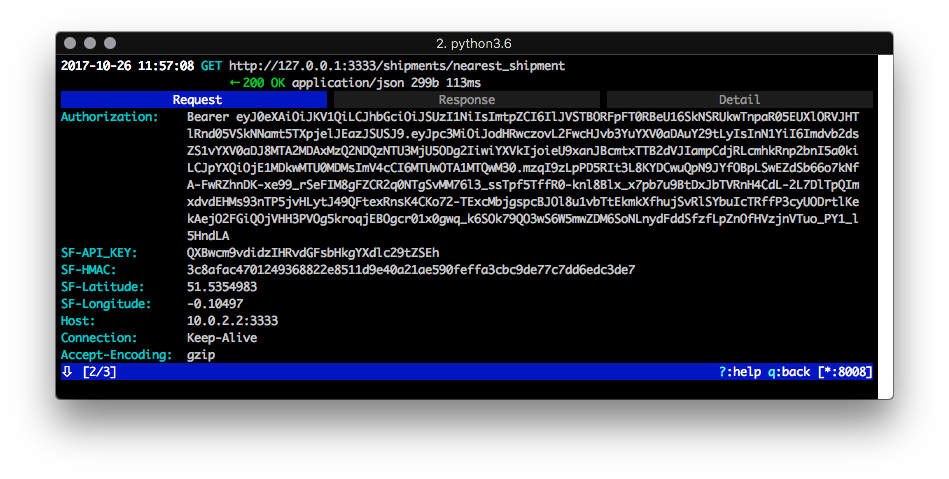
Practical API Security Walkthrough — Part 3
January 17, 2018
Editor's note: This post was originally published in January 2018 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in September 2020. Welcome back! This is the third part of a mini series which uses a fictional product, “ShipFast”, to walk you through the process of defending against various exploits in a mobile application to gain access to data on a remote server allowing real users of the system to gain an unfair business advantage at the expense of the company. Read Full Story
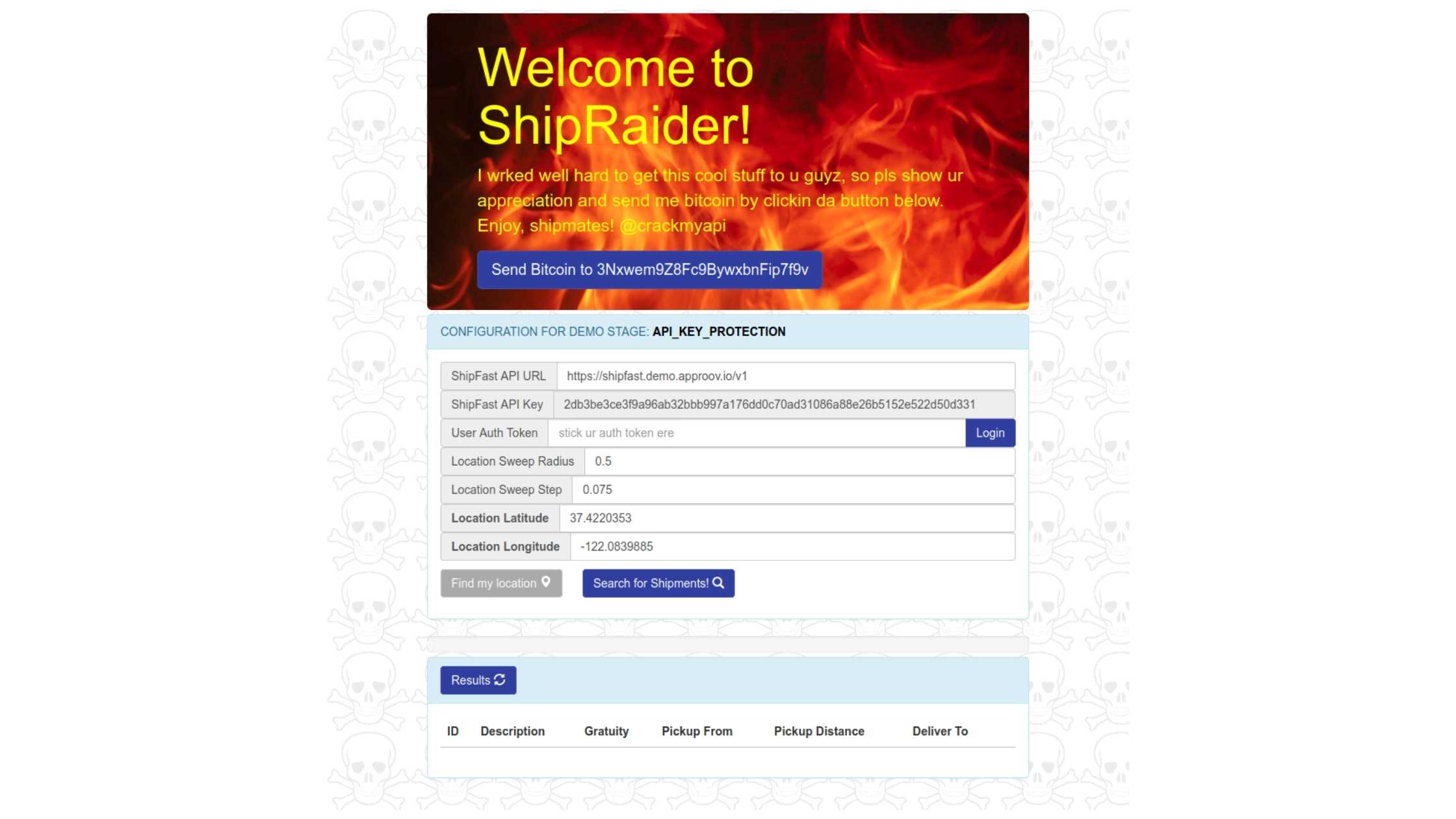
Practical API Security Walkthrough — Part 2
January 16, 2018
Editor's note: This post was originally published in January 2018 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in May 2021. Welcome back! This is the second part of a mini series which uses a fictional product, “ShipFast”, to walk you through the process of defending against various API security exploits in a mobile application to gain access to data on a remote server allowing real users of the system to gain an unfair business advantage at the expense of the company. Read Full Story
