Approov Blog
Mobile App Authentication (6)

Securing Your API server with Approov and Cloudflare
November 19, 2019
Cloudflare is famous among developers as a leading CDN to efficiently deliver customer facing Internet content for their applications, but Cloudflare can also be used to verify all incoming requests before they reach your API server, by leveraging Cloudflare workers. Read Full Story
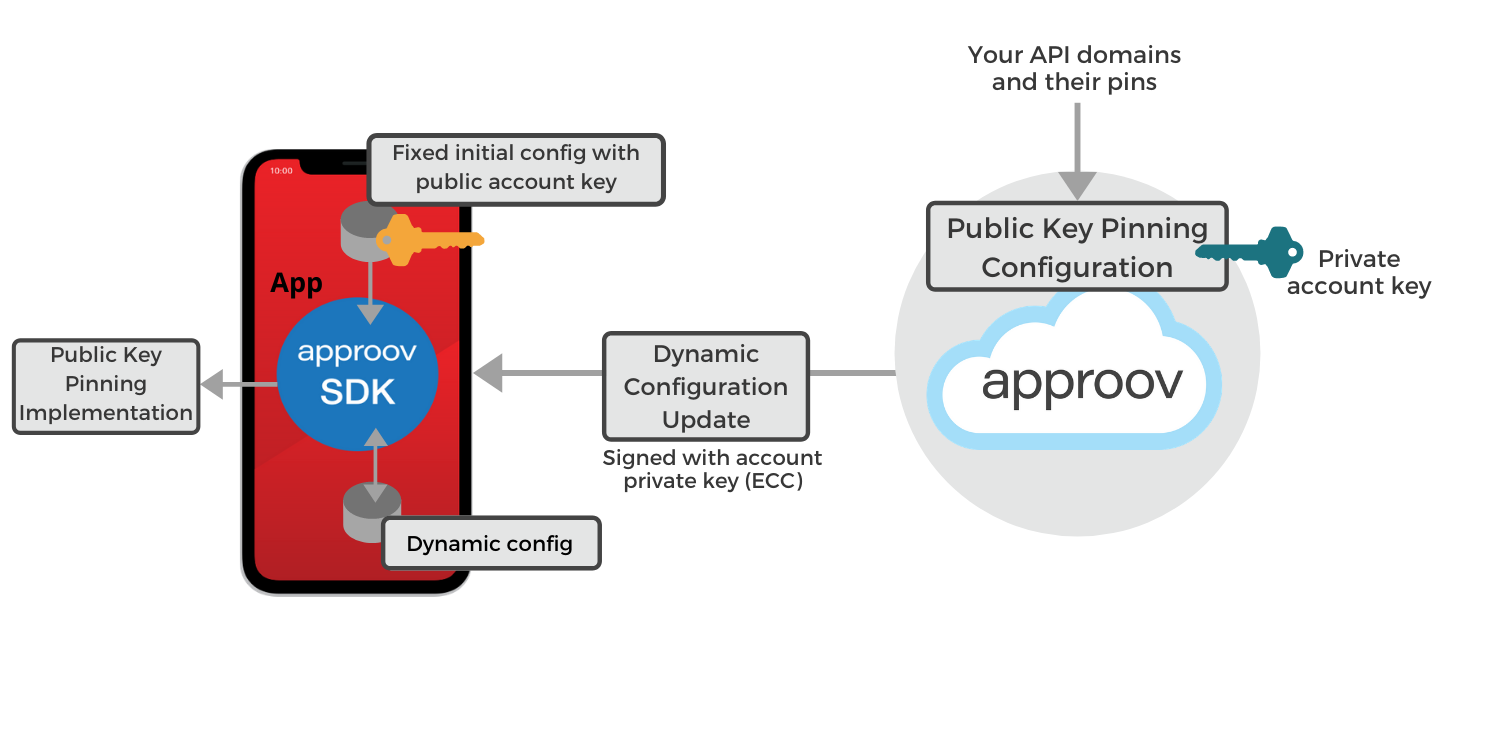
How to Protect Against Certificate Pinning Bypassing
October 15, 2019
Editor's note: This post was originally published in October 2019 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in November 2021. In my previous article, we saw how to bypass certificate pinning within a device you control and in this article we will see how you can protect yourself against such an attack. Read Full Story

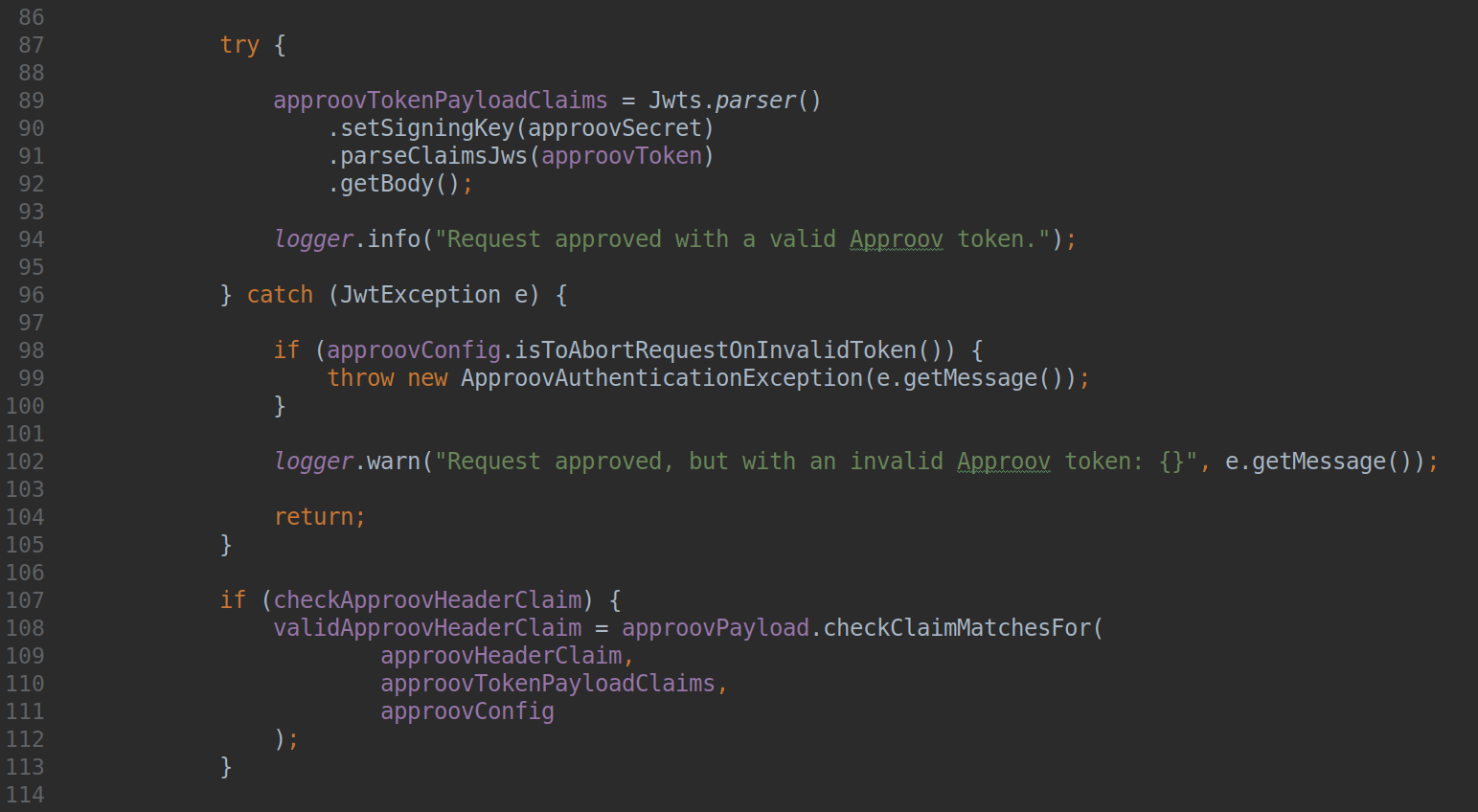
Approov Integration in a Java Spring Stateless API
May 9, 2019
This walk-through will show how simple it is to integrate Approov in a stateless API server using Java and the Spring framework. We will see the requirements, dependencies and a step by step walk-through of the code necessary to implement Approov in a Java Spring stateless API. Read Full Story

Apple DeviceCheck and CriticalBlue Approov
April 27, 2019
We are often asked by customers and prospects to compare our beloved Approov with Apple's DeviceCheck offering. Since DeviceCheck is intended to uniquely identify iOS phone instances then this is a reasonable question. However, DeviceCheck and Approov are designed to do quite different things and therefore we wrote a handy guide to help our customers appreciate when to employ each solution and why. You can download the guide from here. Read Full Story
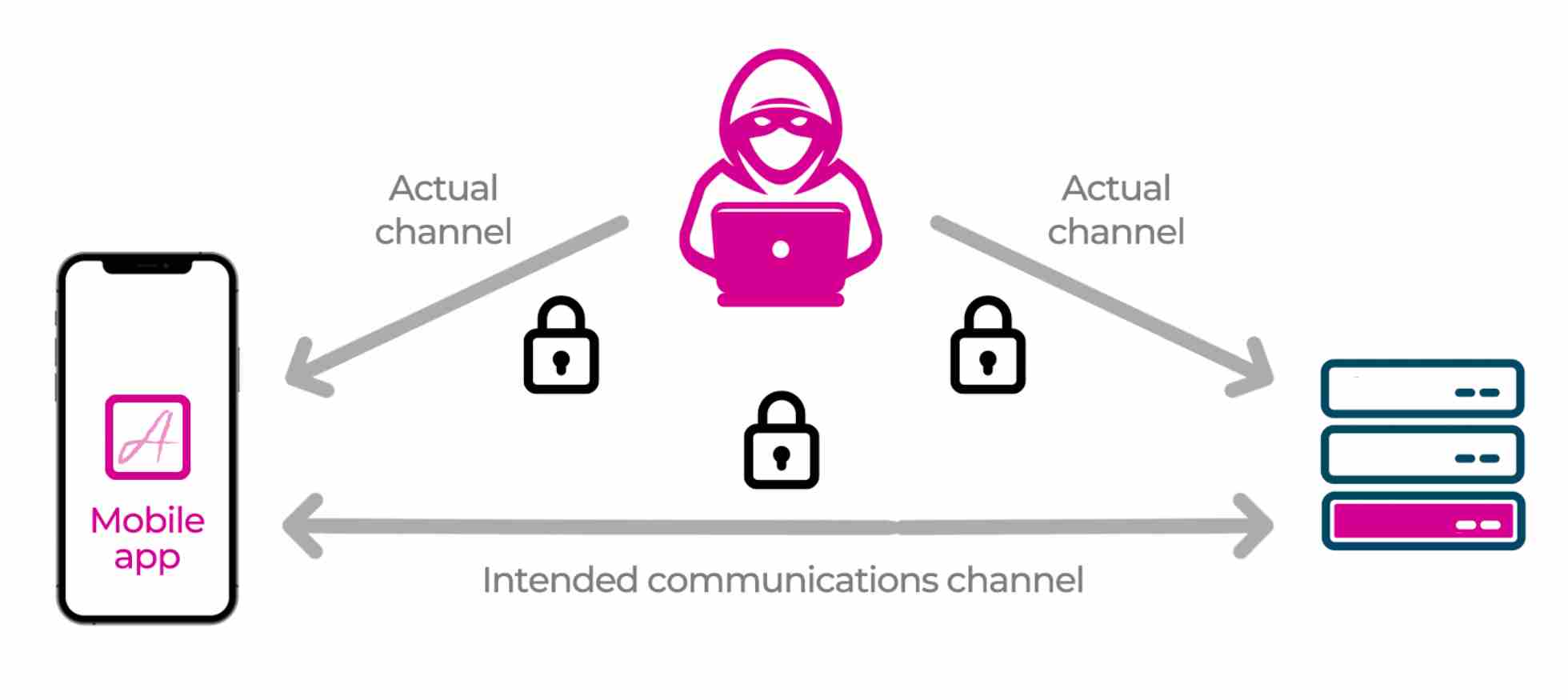
Steal That API Key with a Man in the Middle Attack
April 4, 2019
Editor's note: This post was originally published in April 2019 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in November 2021. As I promised in my previous article, here is the follow up article about performing a man-in-the-middle (MitM) attack to steal an API key, and to follow this article you will need to become the man sitting in the middle of the actual channel, using mitmproxy to help you with the task of stealing the API key. Now it should be clear why MitM stands for man in the middle! Read Full Story

Preventing Mobile App and API Abuse
March 21, 2019
This post includes a video of SKip Hovsmith's talk on preventing mobile app and API abuse at the 2019 AppSec California Conference. Read Full Story

Why Does Your Mobile App Need an API Key?
March 1, 2019
Mobile apps are becoming increasingly important in the strategy of any company. As a result, companies need to release new application versions at a fast pace, and this puts developers under pressure with tight deadlines to complete and release new features very quickly. Read Full Story
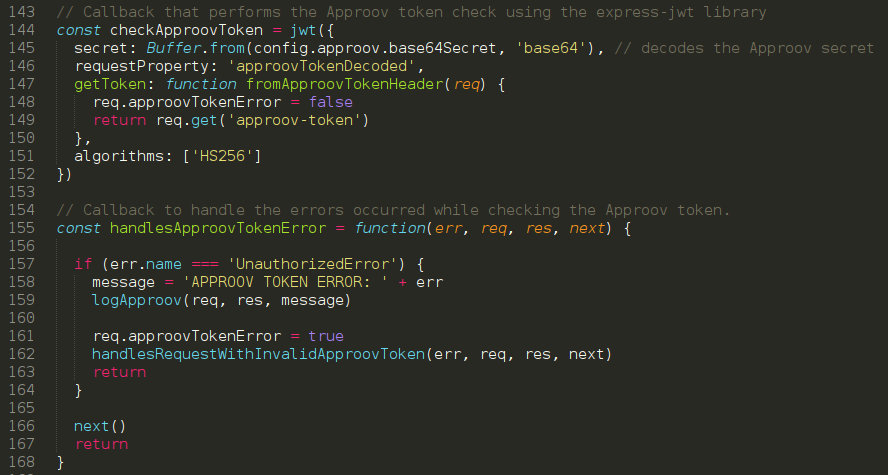
Approov Integration in a NodeJS Express API
February 5, 2019
This walk-though will show us how simple it is to integrate Approov in a current API server using NodeJS and the Express framework. We will see the requirements, dependencies and a step by step walk-through of the code necessary to implement Approov in a NodeJS Express API. Read Full Story
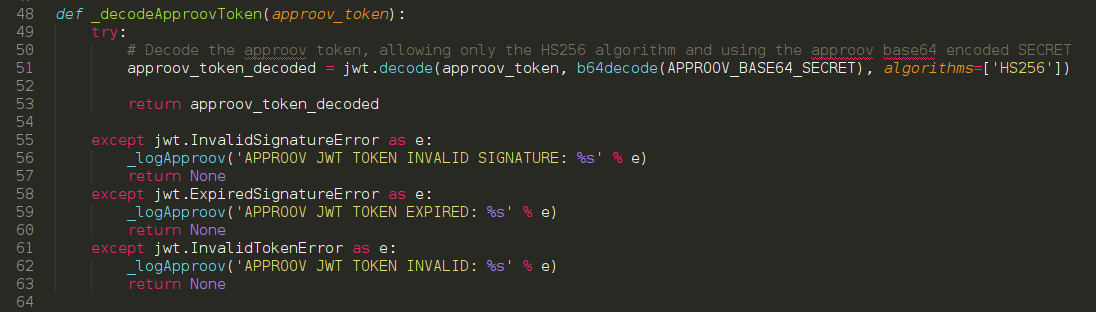
Approov Integration in a Python Flask API
February 4, 2019
This walk-though will show us how simple it is to integrate Approov in a current API server using Python and the Flask framework. We will see the requirements, dependencies and a step by step walk-through over the code necessary to implement Approov in a Python Flask API. Before we tackle the integration of Approov we need first to know how Approov validation is processed in the server and how to setup the environment to follow this walk-through. Note that this article assumes a basic understanding of the Approov mechanics. If you need an overview of that, please read first the Approov Product page. Read Full Story
