Approov Blog
Third Party APIs

FHIR API Security Research- 3 Actions for Mobile Healthcare Companies
November 22, 2021
Considering the recent “Playing with FHIR” research report together with the earlier “All that We Let In” research report (which looked at the state of mHealth app/API security), it would be understandable if healthcare organizations were unsure of what immediate actions they should take. In this article we will focus on healthcare service companies who have patient or clinician mobile apps, for whom we will recommend 3 immediate steps which should be taken today. Read Full Story

FHIR API Security Research Sparks Debate
November 9, 2021
Alissa Knight released her report “Playing with FHIR” a couple of weeks ago (download it here) about her investigations into the security of healthcare apps and APIs which use the FHIR standard. This report has certainly sparked a lot of debate about the security of healthcare apps and a broader discussion about who is accountable for keeping patient data safe as the ecosystem expands. The bottom-line is that everyone in the healthcare ecosystem needs to take steps to shield their APIs immediately. Read Full Story
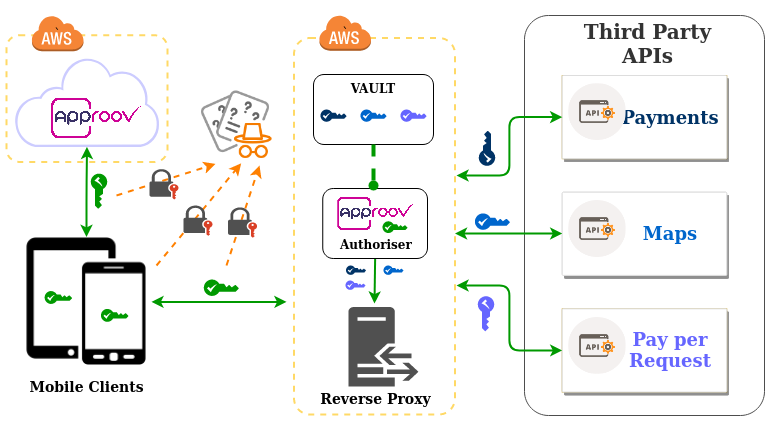
Approov Serverless Reverse Proxy in the AWS API Gateway
February 27, 2020
In my previous article, Using a Reverse Proxy to Protect Third Party APIs, I left you without a solution to secure the purple API key inside the mobile devices in the graphic above from being extracted by the bad guy wearing the orange hat. As promised I am going to show you in this article how you can implement a solution for it. Rather than securing the purple API key, wouldn’t it be better not to have it in the first place or at least to make sure that if it is extracted then it can’t be used at scale by malicious actors? Well that's what a Mobile App Attestation solution is for, and we will start this article by explaining what it is. Spoiler alert: it allows you to secure your API without needing to ship any type of secret inside your mobile app or, if you already have a secret in your mobile app, it allows you to ensure that the secret can’t be used to abuse your API. Read Full Story
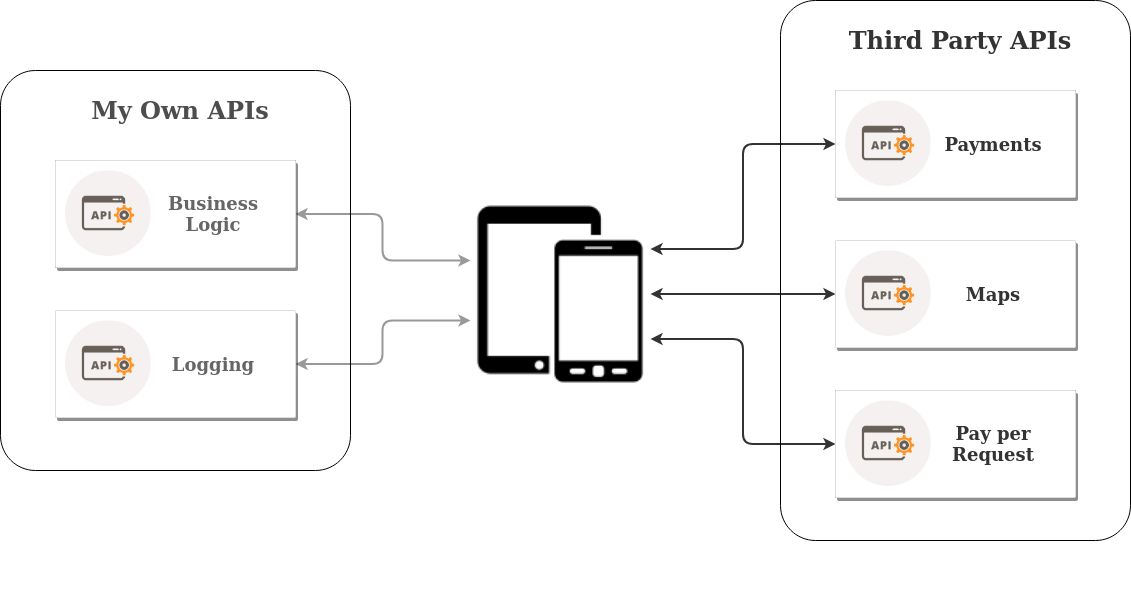
Using a Reverse Proxy to Protect Third Party APIs
February 12, 2020
In this article you will start by learning what Third Party APIs are, and why you shouldn’t access them directly from within your mobile app. Next you will learn what a Reverse Proxy is, followed by when and why you should use it to protect the access to the Third Party APIs used in your mobile app. Read Full Story
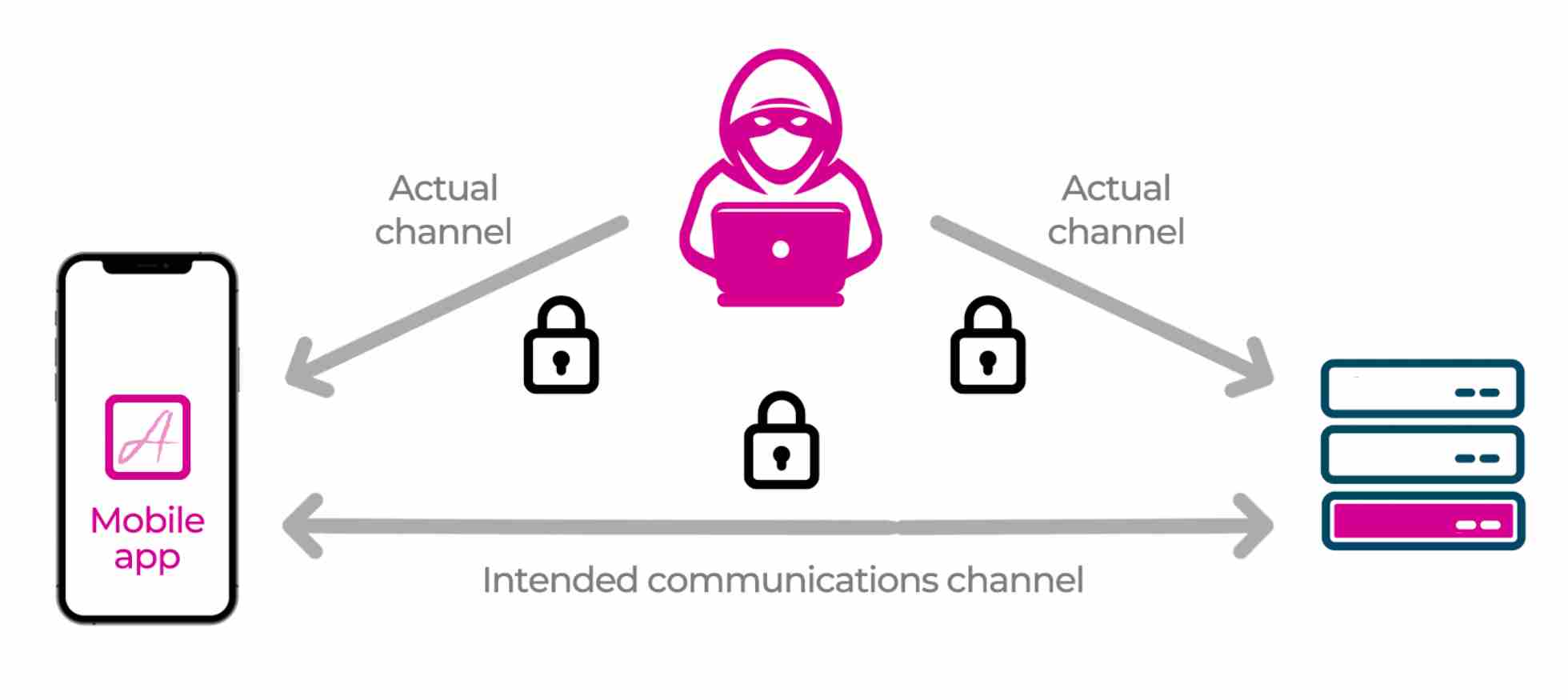
Steal That API Key with a Man in the Middle Attack
April 4, 2019
Editor's note: This post was originally published in April 2019 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in November 2021. As I promised in my previous article, here is the follow up article about performing a man-in-the-middle (MitM) attack to steal an API key, and to follow this article you will need to become the man sitting in the middle of the actual channel, using mitmproxy to help you with the task of stealing the API key. Now it should be clear why MitM stands for man in the middle! Read Full Story

Whitelists & Indirection Go Together Like Chocolate and Peanut Butter
July 28, 2017
source: nourishmorelove Used properly, whitelisting is a simple and effective security tactic to minimize attack surfaces. If you’re not on the list, you don‘t get in. No exceptions. Smooth as chocolate. If it’s too easy for you to find and spoof a name on the list, use indirection to make it harder. Sticky as peanut butter. Together they taste great. Read Full Story
Help Your Mobile API Ecosystem to Flourish
July 5, 2017
(Image via http://maxpixel.freegreatpicture.com) The API for a service faces conflicting demands in order to deliver value to end users. It needs to be open to allow innovation by 3rd party app developers. This is necessary to meet niche customer needs and open new markets for your service beyond what an in house app development team could provide. Read Full Story

API Key Security with Approov
December 20, 2016
Are you an API consumer? Or, in other words, do your mobile apps use external APIs to provide content and functionality that engages with and excites your customers? If so, how do you prevent bad actors from stealing, or otherwise misusing, your access permissions? API security is a major challenge today. Read Full Story
