David Stewart
- Advisor at Approov / Former CEO of Approov
30+ years experience in security products, embedded software tools, design services, design automation tools, chip design.
Approov Blog

Security Key to mHealth Success
July 23, 2020
In 2016, mHealth apps were the third fastest-growing category of apps behind games and utilities. In 2017, the number of healthcare applications available for smartphone users doubled from that of 2015 to 325,000, from 84,000 different publishers, with an estimated 3.7 billion downloads that year. By 2018, nearly a third of all patients were using their mobile phone for health-related searches and for booking appointments, an overwhelming 99% of consumers believed that mHealth apps improved their quality of life and 70% of millennials were interested in a mobile app that would help them actively manage their well-being. By 2027, mHealth app usage among patients is projected to grow at a 10-year CAGR of 40%. Read Full Story
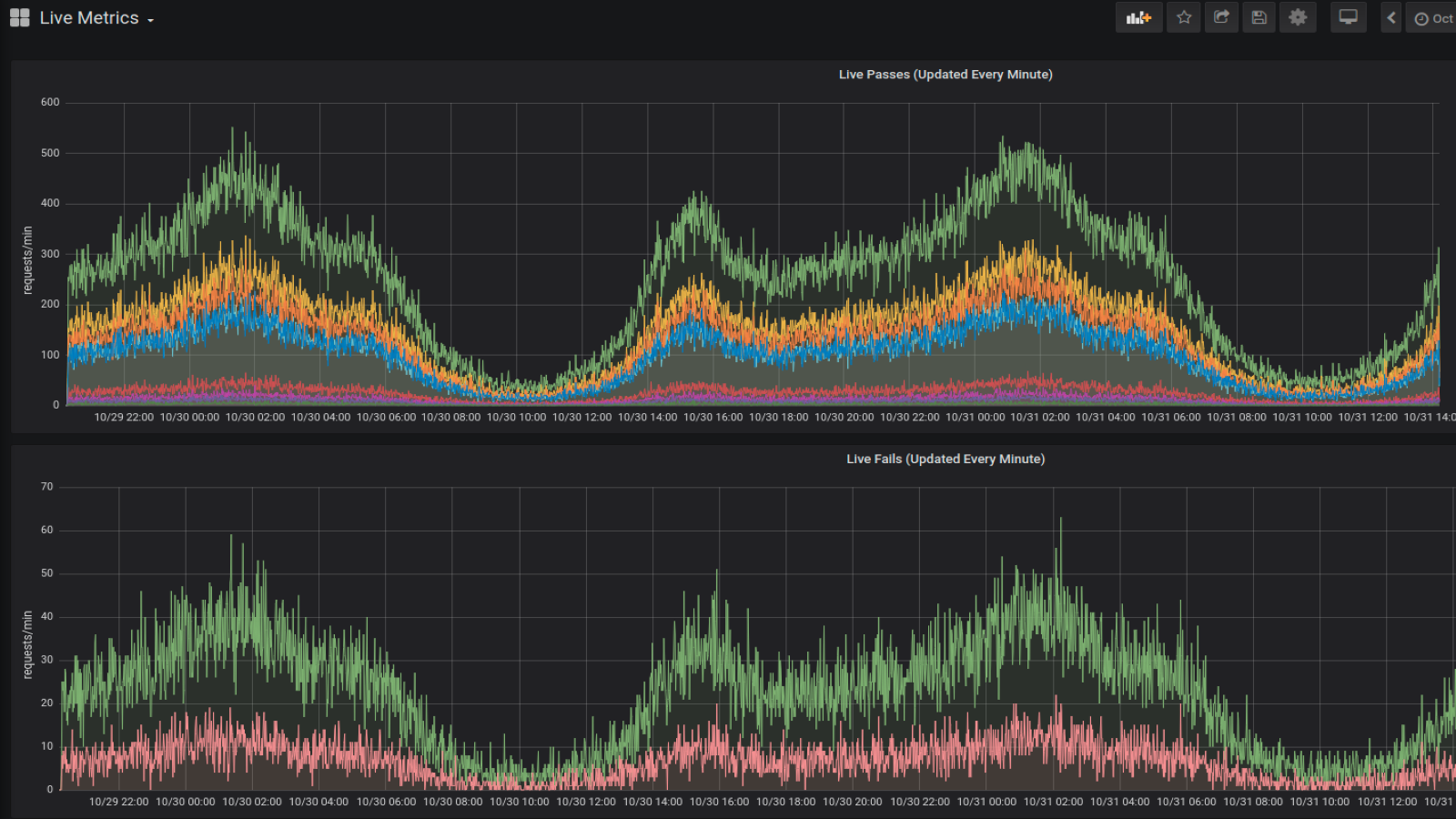
A Short Tour of the Approov Metrics
July 17, 2020
Approov API Threat Protection protects the APIs which service your mobile apps from abuse and fraud by unauthorized bad actors. We talk to customers about how Approov authenticates genuine mobile app instances without requiring hidden secrets or design decision making in the app. We discuss the simplicity of integrating it into your app and deploying it in production. We even talk about the scalability, redundancy and resilience built into the Approov cloud service. However, what we don’t talk enough about is our metrics, a required feature to monitor and manage your service. With this article, we will give our metrics the description they deserve. Read Full Story

Approov Dynamic Pinning - An Independent View
June 26, 2020
Our friends at Rakuten have written a blog about their opinions of and experiences with the Approov dynamic pinning capability. You can read it here. It’s always nice to be able to point at independent material about Approov because, although we think very highly of it, we may be somewhat biased! Read Full Story

Six Reasons to Choose SaaS Security Over In-house
June 16, 2020
Spending large amounts of money on in-house security may not yield as great a reduction in risk as you might hope. A big investment might only result in marginal improvements -- especially with the high price of cyber security labour in the current skills shortage. Finding the right mix of security options is something of a balancing act, and cloud-based security or SaaS security (Security as a Service, or SECaaS) can offer an alternative. Read Full Story
Protecting Your SDK With Approov
June 11, 2020
Photo by Ann H from Pexels When we talk about Approov API Threat Protection, we usually talk about it in the context of ensuring that only genuine instances of your own mobile app can use your API to access your backend servers. However, there is another use case which occurs commonly in our customer base - ensuring that only your SDK can use your API where you distribute your SDK to your customers. Here also, Approov is highly effective. Read Full Story

Vulnerabilities In Fintech Mobile Apps
May 22, 2020
Mobile applications play an increasingly important role in our lives -- and the current global lockdown due to the COVID-19 situation has led to a surge in the download of financial technology or fintech apps. According to research by the deVere Group, the coronavirus pandemic has fuelled a massive 72% rise in the use of fintech apps in Europe. But while this spike in adoption and usage provides encouraging news for the fintech industry, these mobile apps present a real threat, with hackers looking for new ways to bypass software defences, or to exploit security vulnerabilities. Read Full Story

Mobile Auction Apps: Scalping And Sniping
May 6, 2020
The eBay concept first came to light as a browser based auction platform, giving sellers a chance to offer their goods to potential buyers from across the globe, before making the transition to become one of the world’s most popular mobile auction apps. Others have since emerged, with mobile auction apps giving event organisers the tools to simplify setup and management, and buyers the simplicity and speed of making bids and performing transactions with the swipe of a finger. Of course, every financial opportunity throws itself open to dishonest practices -- and mobile auction apps are no exception. Scalping and sniping are two of the major issues faced by mobile auction operators. Read Full Story

Protecting Personal Information & Sensitive Data In Mobile Health Apps
April 20, 2020
Recent years have seen a move towards cloud platforms and mobile health apps for citizens -- applications and data processing systems that enable ordinary people to interact with their health providers, make appointments with medical professionals, order prescriptions, and gain on-demand access to their medical records. The ongoing COVID-19 pandemic is putting greater emphasis on this trend, as citizens clamour for the latest news, advice, and best practices, while government and health organisations look to digital technologies to help them develop treatment protocols, track the progress of the virus spread, and monitor the condition of all those affected. Read Full Story

Securing the Enterprise for Remote Work
April 2, 2020
At a time when the world could use some good news, any good news, the central health crisis continues to get compounded by a persistent wave of cyberattacks targeted at companies and their employees. Not even healthcare institutions and agencies at the center of responding to the emergency have been spared, with the World Health Organization, the U.S. Department of Health and Human Services and even a UK-based coronavirus testing facility being targeted by cyber profiteers. Read Full Story

Top 5 Threats to APIs Servicing Mobile Apps
March 29, 2020
As mobile apps become increasingly paramount to operating successfully in today’s markets, a big question mark over API security is raised. Gartner has previously predicted that by 2022, “API abuses will be the most-frequent attack vector resulting in data breaches for enterprise web applications.” Since every mobile app out there is powered by APIs, securing them is clearly a top priority. Read Full Story
