Approov Blog
Mobile App Security (2)

“Mobile First” is for Mobile Secrets, Too
January 16, 2024
This is the second article in a guest blog series from Intellyx. You can read the first article here. Organizations, such as the Citi Consumer Bank when I was head of security architecture there, adopt a “mobile first” approach to application development. “Mobile first” means first developing a mobile application that delivers a great customer experience, and later focusing on developing other customer facing applications (such as a web app). Read Full Story

2024: Reflecting on a Dynamic, Tumultuous Cyber Year
January 16, 2024
As we step into 2024, it's crucial to reflect on the cyber landscape of the past year, marked by significant breaches that underscore the persistent challenges in securing our digital lives. Here are some notable incidents that grabbed headlines: Read Full Story

Approov Addresses Apple Watch Security Issues
December 18, 2023
Apple and MIT recently published a study indicating that 2.6 billion personal records were exposed through data breaches over the last two years. These findings underscore the need for protecting data in the cloud through mobile attestations and improved API security. Watches, wearables and other new types of mobile devices are now the weakest link in the mobile app threat landscape. Approov addresses this threat head on with Release 3.2 of the solution. While Release 3.2 includes other important enhancements (detailed in the Press Release), this blog specifically explores the crucial advancements made to enhance the security of the Apple Watch. Read Full Story

Understanding the Security of Mobile Apps in Africa
November 29, 2023
CyLab-Africa researchers partner with mobile security provider for summer collaboration experience Researchers from CyLab-Africa and the Upanzi Network recently partnered with the mobile security provider Approov to explore the security of common financial services apps used across Africa. After surveying 224 popular financial applications, the researchers found that 95 percent of these Android apps exposed secrets that can be used to reveal personal and financial data. Across these applications, approximately 272 million users have the potential to be victims of the security flaws. Read Full Story

The Rise of Super Apps: Challenges & Opportunities in Mobile Security
November 9, 2023
In recent years, the tech world has witnessed a significant shift towards what are known as "super apps." These mobile applications have become increasingly popular, offering a plethora of services within a single, convenient platform. While they present numerous opportunities for users and businesses, they also bring forth a set of unique challenges, particularly in the realm of mobile security. Read Full Story
The Critical Need to Defend Against Unauthorized Apps
October 27, 2023
Safeguarding Security and Integrity: In today's digital landscape, mobile applications have become integral to our daily lives, offering convenience, entertainment, and essential services. However, with the rise of mobile app usage, there's also been a surge in unauthorized and malicious apps (aka Dummy Apps, Cloned Apps, Tampered Apps) that pose significant threats to users, organizations, and developers alike. In this blog post, we'll explore why it's imperative for developers to prevent the running of non-authorized apps from accessing your API’s and how cutting-edge solutions like Approov Mobile Security can help safeguard security and integrity. Read Full Story

Approov Publishes Carnegie-Mellon University CyLab-Africa Report on Mobile App Security in Africa
October 12, 2023
This is a Guest Blog written by the CyLab-Africa team : Theoneste Byagutangaza, Lena Chacha, Trevor Henry Chiboora, Joel Jefferson Musiime and George McGregor from Approov. This week, we published a new report: “The Security Challenges of Financial Mobile Apps in Africa”. This is based on research carried out by a research team from CyLab-Africa, sponsored by Approov. The research reveals an alarming Fintech exposure in Africa – 95% of the apps investigated leak secrets! The full report is published on the Approov website here and is essential reading for any mobile app developers who are planning worldwide deployment. Read Full Story

Reducing the Cost of Data Breaches with Approov Mobile Security
August 3, 2023
Introduction Data breaches have become a persistent threat for organizations across the globe, with cybercriminals relentlessly targeting valuable data, sensitive customer information, and proprietary business data. The data below is alarming, but the key takeaway is through prevention, monitoring, and rapid remediation, costs can be eliminated or highly mitigated. Read Full Story
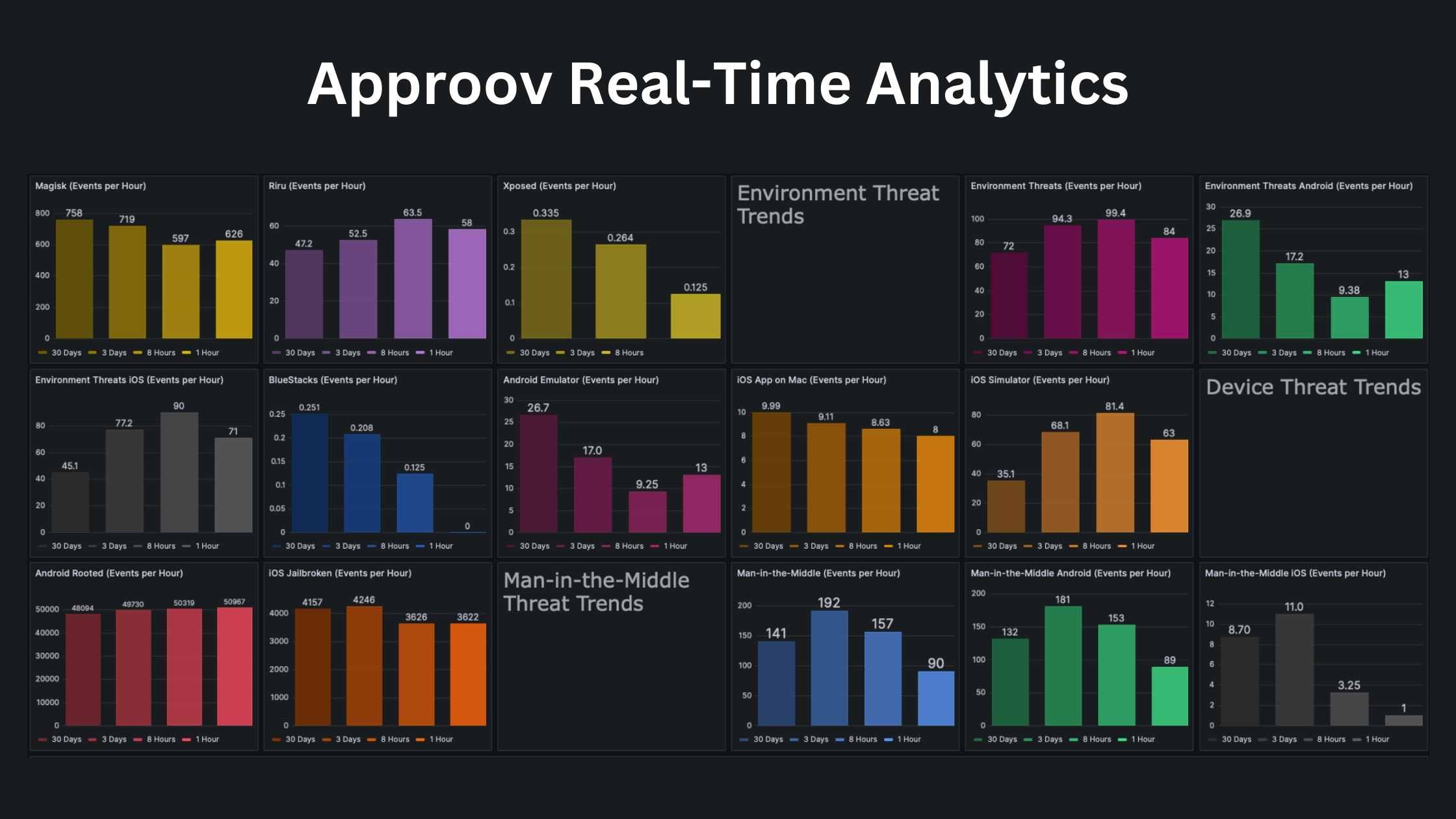
Staying Ahead of Mobile App Threats with Real-Time Analytics
August 1, 2023
Mobile apps and APIs are increasingly being targeted by cybercriminals using sophisticated techniques to exploit vulnerabilities and gain access to sensitive data. To stay ahead of these threats, real-time analytics on the security state of mobile apps and devices is critical. Read Full Story

How To Use a MitM Attack to Bypass Code Obfuscation to Extract Secrets From the ChatGPT Mobile App
June 23, 2023
In a previous article, we saw how to use code obfuscation to make it more difficult for an attacker to extract a secret through static binary analysis of the ChatGPT demo mobile app. However, it's important to note that code obfuscation is not always as effective in protecting secrets as we might hope. It can give a false sense of security, similar to the Maginot Line that the French built during World War II to deter the German invasion of France. As many know, the German military simply went around the Maginot Line and quickly invaded France, rendering it useless. This event is now often used as an analogy for situations where something provides a false sense of security rather than actual security. Read Full Story
