Paulo Renato
Paulo Renato is known more often than not as paranoid about security. He strongly believes that all software should be secure by default. He thinks security should be always opt-out instead of opt-in and be treated as a first class citizen in the software development cycle, instead of an after thought when the product is about to be finished or released.
Approov Blog
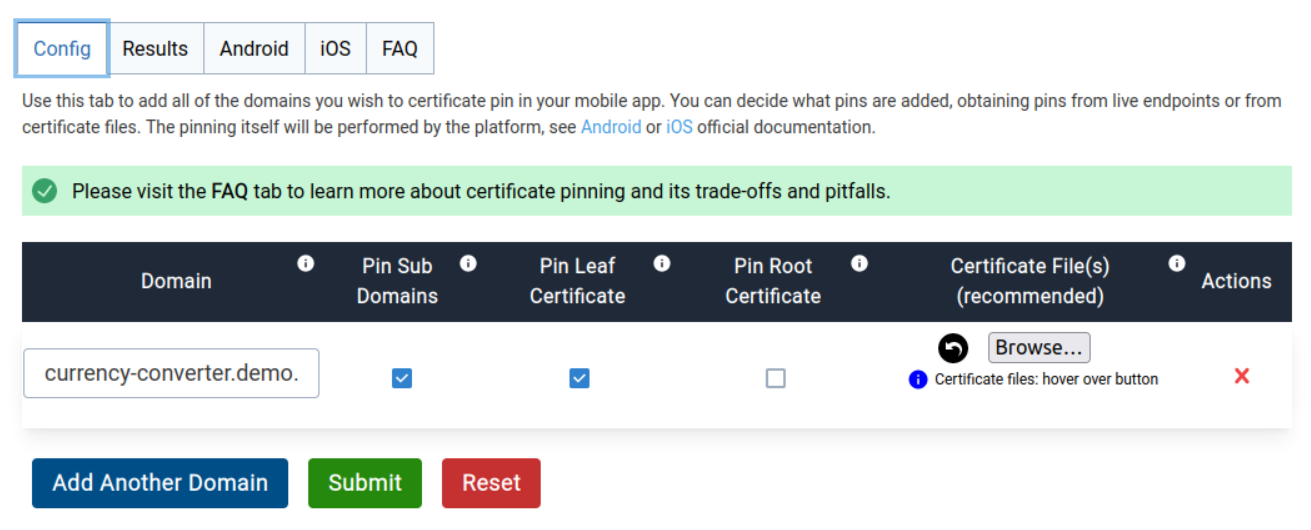
Securing HTTPS with Certificate Pinning on Android
June 26, 2019
Editor's note: This post was originally published in June 2019 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in November 2021. In a previous article we saw how we could steal an API key by performing a man in the middle (MitM) attack to intercept the HTTPS traffic between the mobile app and the API server. In this article we will learn how to mitigate this type of attack by using a technique known as certificate pinning. Read Full Story
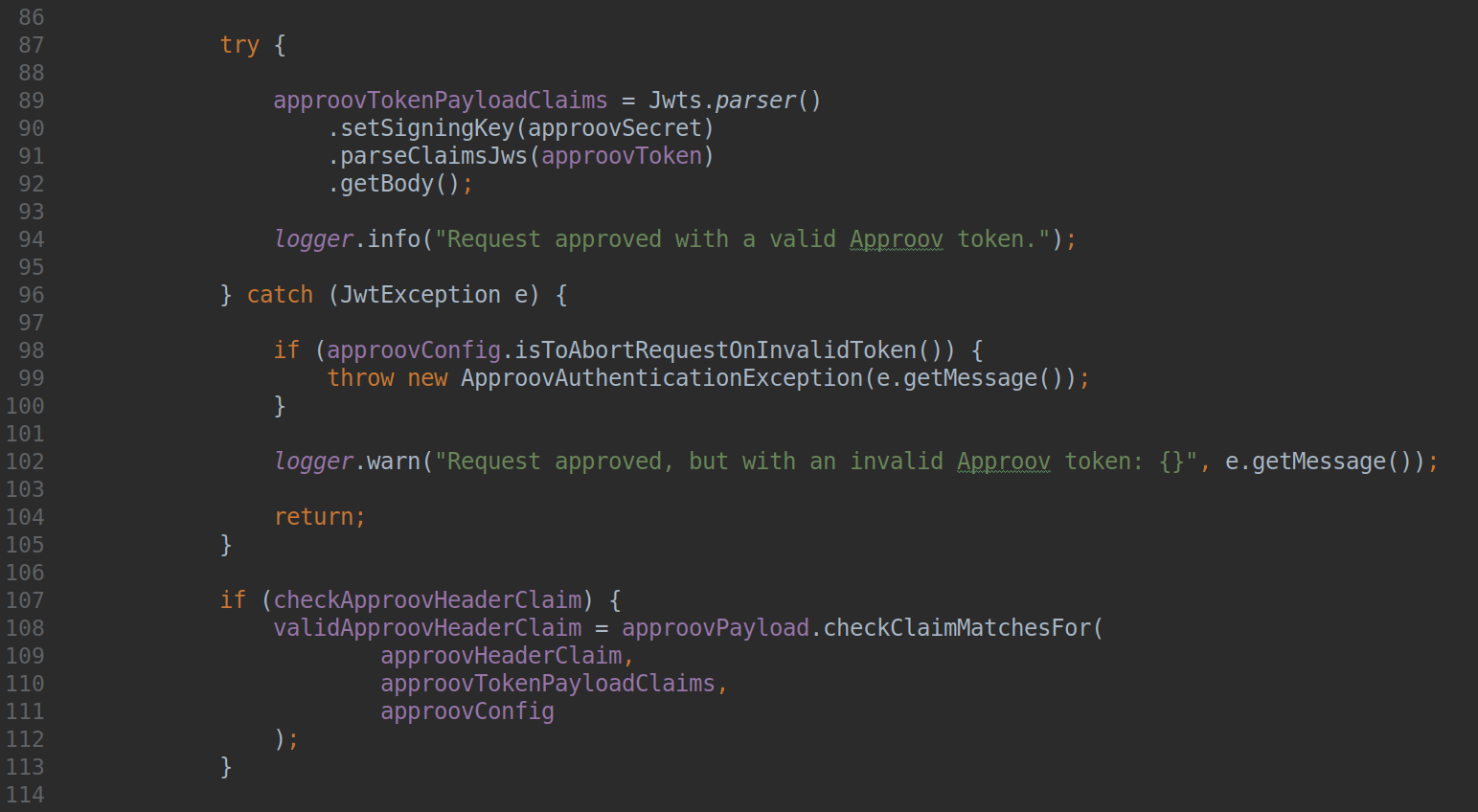
Approov Integration in a Java Spring Stateless API
May 9, 2019
This walk-through will show how simple it is to integrate Approov in a stateless API server using Java and the Spring framework. We will see the requirements, dependencies and a step by step walk-through of the code necessary to implement Approov in a Java Spring stateless API. Read Full Story
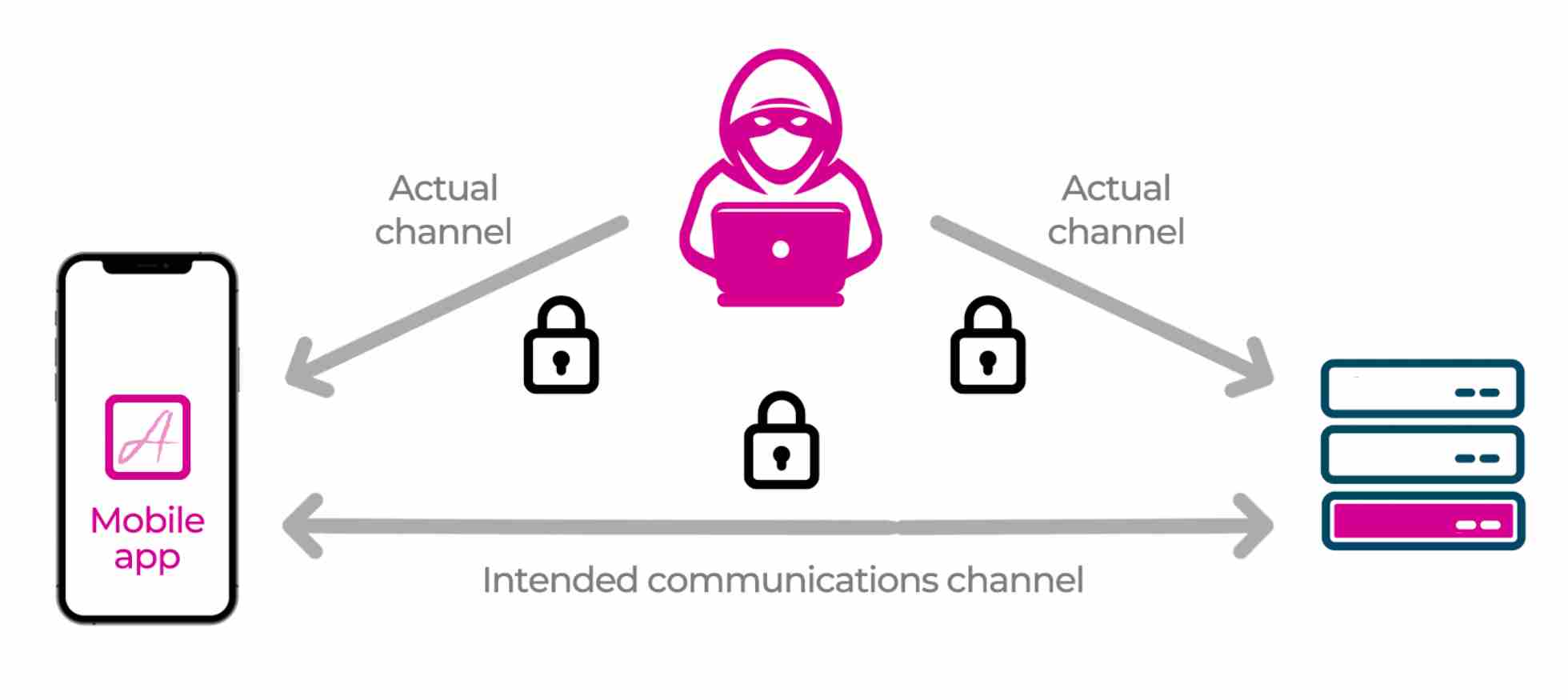
Steal That API Key with a Man in the Middle Attack
April 4, 2019
Editor's note: This post was originally published in April 2019 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in November 2021. As I promised in my previous article, here is the follow up article about performing a man-in-the-middle (MitM) attack to steal an API key, and to follow this article you will need to become the man sitting in the middle of the actual channel, using mitmproxy to help you with the task of stealing the API key. Now it should be clear why MitM stands for man in the middle! Read Full Story
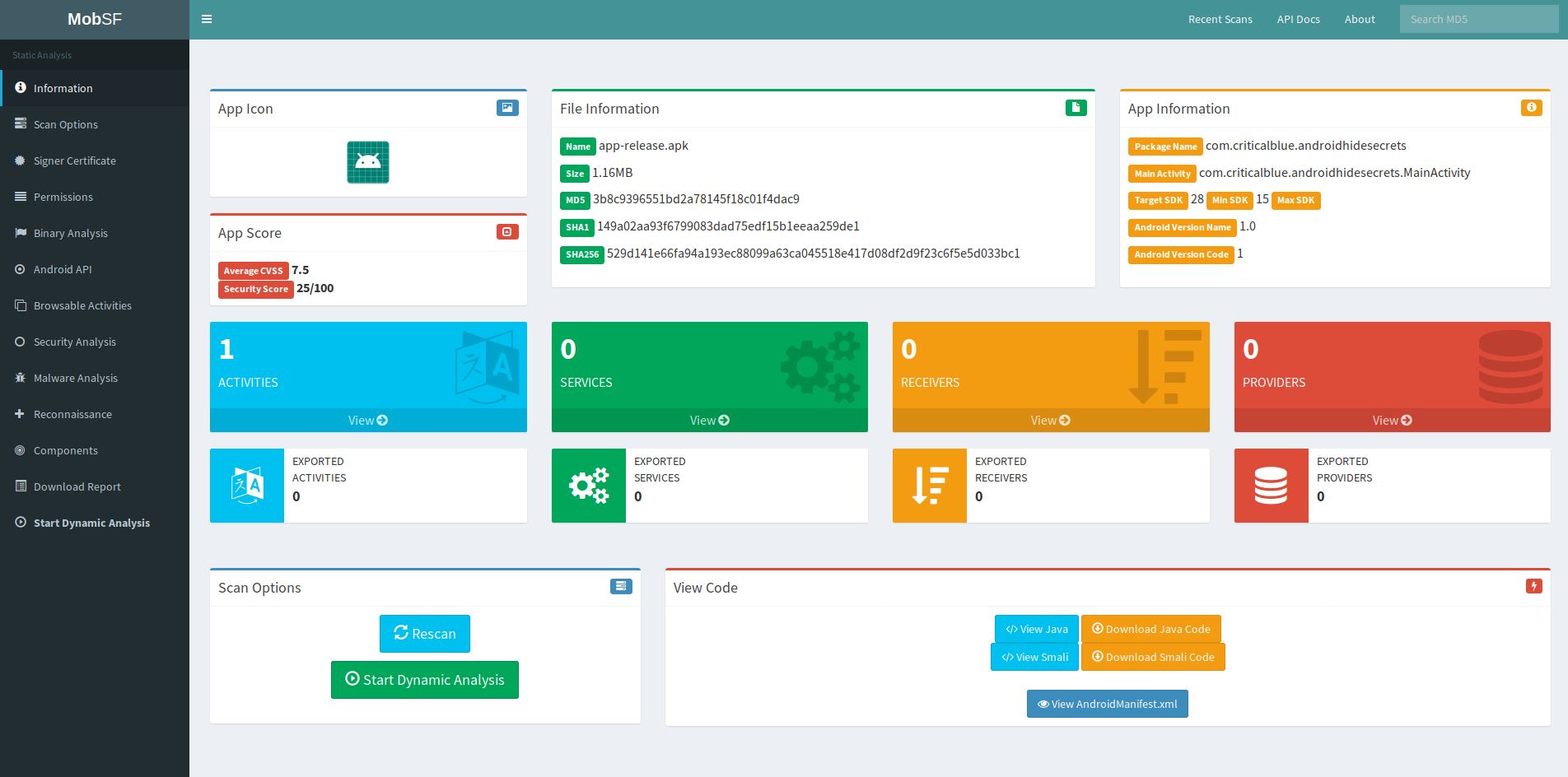
How to Extract an API Key from a Mobile App by Static Binary Analysis
March 14, 2019
An API key is probably the most common method used by developers to identify what is making the request to an API server, but most developers are not aware how trivial it is for a hacker or even a script kiddie to steal and reuse an API key in order to gain unauthorized access to their APIs. In the previous article we saw why your mobile app needs an API key, and now we will see how to grab that API key from your mobile app by reverse engineering the binary in an effective and quick way with an open source tool. Once we see how easy it can be done, we will realize that it is even achievable by non-developers. Read Full Story

Why Does Your Mobile App Need an API Key?
March 1, 2019
Mobile apps are becoming increasingly important in the strategy of any company. As a result, companies need to release new application versions at a fast pace, and this puts developers under pressure with tight deadlines to complete and release new features very quickly. Read Full Story
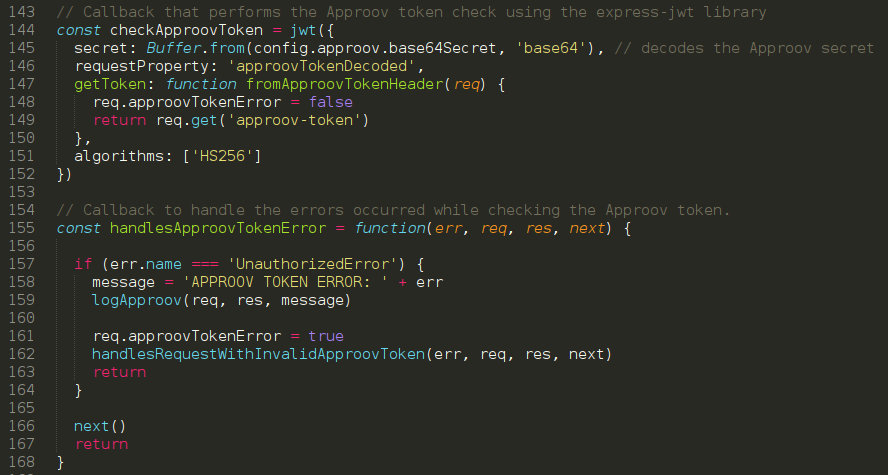
Approov Integration in a NodeJS Express API
February 5, 2019
This walk-though will show us how simple it is to integrate Approov in a current API server using NodeJS and the Express framework. We will see the requirements, dependencies and a step by step walk-through of the code necessary to implement Approov in a NodeJS Express API. Read Full Story
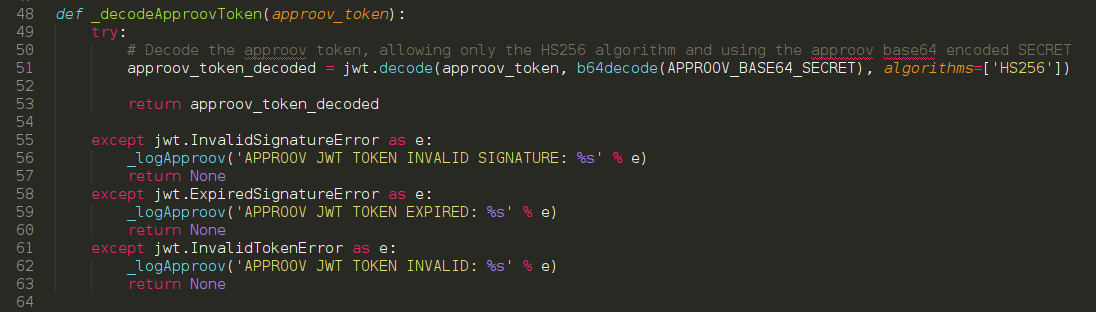
Approov Integration in a Python Flask API
February 4, 2019
This walk-though will show us how simple it is to integrate Approov in a current API server using Python and the Flask framework. We will see the requirements, dependencies and a step by step walk-through over the code necessary to implement Approov in a Python Flask API. Before we tackle the integration of Approov we need first to know how Approov validation is processed in the server and how to setup the environment to follow this walk-through. Note that this article assumes a basic understanding of the Approov mechanics. If you need an overview of that, please read first the Approov Product page. Read Full Story

The Top 6 Mobile API Protection Techniques - Are They Enough?
December 22, 2018
APIs are a necessary and central part of the strategy of any digital business that wants to stay competitive and monetize its assets. Additionally, end users’ form factor of choice when using digital services is now firmly mobile. The trend towards APIs and mobile devices has moved the attack surface in a significant way and digital businesses must adapt and evolve their security policies accordingly. Read Full Story

Is Your Mobile App Leaking Secrets?
October 30, 2018
In Why Exposed API Keys and Sensitive Data are Growing Cause for Concern, Janet Wagner points out that the exposure of sensitive data through code is a growing cause of concern as developers rely more and more on the cloud for the overall workflow during development and deployment of their applications and in accessing third part services at run-time from within them. Read Full Story
