Paulo Renato
Paulo Renato is known more often than not as paranoid about security. He strongly believes that all software should be secure by default. He thinks security should be always opt-out instead of opt-in and be treated as a first class citizen in the software development cycle, instead of an after thought when the product is about to be finished or released.
Approov Blog

Approov Integration for PHP Backends
October 23, 2020
Photo by Ben on Unsplash PHP was created in 1994 by the Danish-Canadian developer Rasmus Lerdorf. In its first incarnation PHP was a simple set of Common Gateway Interface (CGI) binaries, written in the C programming language, which Rasmus used to track visitors to his online CV. This explains why PHP originally stood for Personal Home Page but from PHP 3 onwards it became a recursive acronym that stands for Hypertext Processor. Read Full Story

Approov Integration for Ruby Backends
October 22, 2020
Photo by Victoria Priessnitz on Unsplash Ruby is a programming language conceived by Yukihiro Matsumoto from Japan in 1993 and released in 1995. The language is intended to make the developer more productive by focusing on making it easier to parse by humans than by computers. Ruby is a blend of the best parts of the author's favourite languages: Perl, Smalltalk, Eiffel, Ada and Lisp. Read Full Story

Approov Cloudflare Worker Quickstart
August 14, 2020
Cloudflare started as a CDN that quickly became popular among developers due to its efficiency in delivering customer facing Internet content from a closer location to the end user than the real location of the backend server. Here is how to integrate Approov token checking into it. Read Full Story

Approov Integration with Kong API Gateway
May 20, 2020
API Gateways have become very popular for deploying APIs at scale because they sit between the client and the API server backend This enables all kinds of integrations without the need to modify the API code itself, and that’s exactly what Kong API Gateway excels at. Read Full Story

Approov Integration With NGINX Plus
May 14, 2020
Photo by James Wheeler from Pexels NGINX first gained popularity as a fast and efficient web server with cache, load balancing and reverse proxy capabilities. With the evolution to NGINX Plus it gained additional capabilities, such as acting as an API Gateway with built in security controls. These security controls can be further extended via dynamic modules and we will utilise them to integrate Approov into the platform without changing any API code. Read Full Story
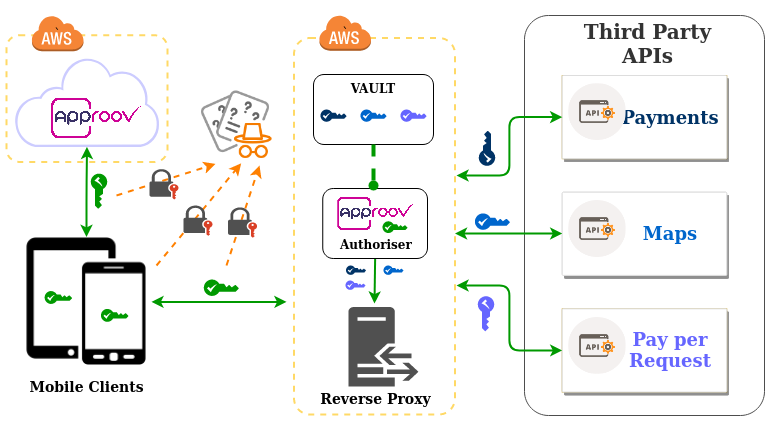
Approov Serverless Reverse Proxy in the AWS API Gateway
February 27, 2020
In my previous article, Using a Reverse Proxy to Protect Third Party APIs, I left you without a solution to secure the purple API key inside the mobile devices in the graphic above from being extracted by the bad guy wearing the orange hat. As promised I am going to show you in this article how you can implement a solution for it. Rather than securing the purple API key, wouldn’t it be better not to have it in the first place or at least to make sure that if it is extracted then it can’t be used at scale by malicious actors? Well that's what a Mobile App Attestation solution is for, and we will start this article by explaining what it is. Spoiler alert: it allows you to secure your API without needing to ship any type of secret inside your mobile app or, if you already have a secret in your mobile app, it allows you to ensure that the secret can’t be used to abuse your API. Read Full Story
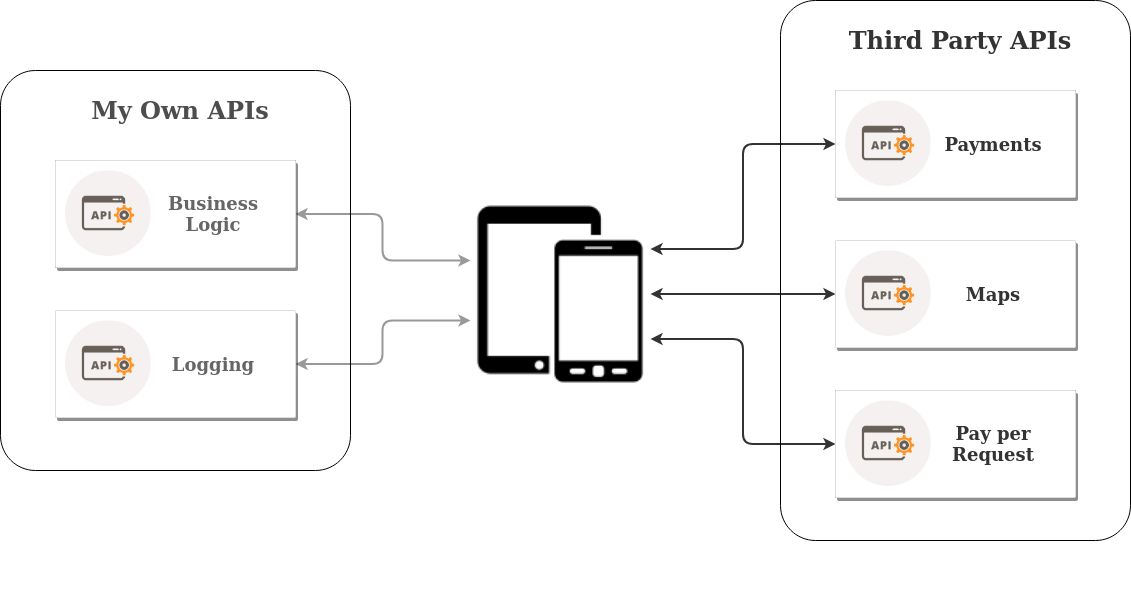
Using a Reverse Proxy to Protect Third Party APIs
February 12, 2020
In this article you will start by learning what Third Party APIs are, and why you shouldn’t access them directly from within your mobile app. Next you will learn what a Reverse Proxy is, followed by when and why you should use it to protect the access to the Third Party APIs used in your mobile app. Read Full Story

Securing Your API server with Approov and Cloudflare
November 19, 2019
Cloudflare is famous among developers as a leading CDN to efficiently deliver customer facing Internet content for their applications, but Cloudflare can also be used to verify all incoming requests before they reach your API server, by leveraging Cloudflare workers. Read Full Story
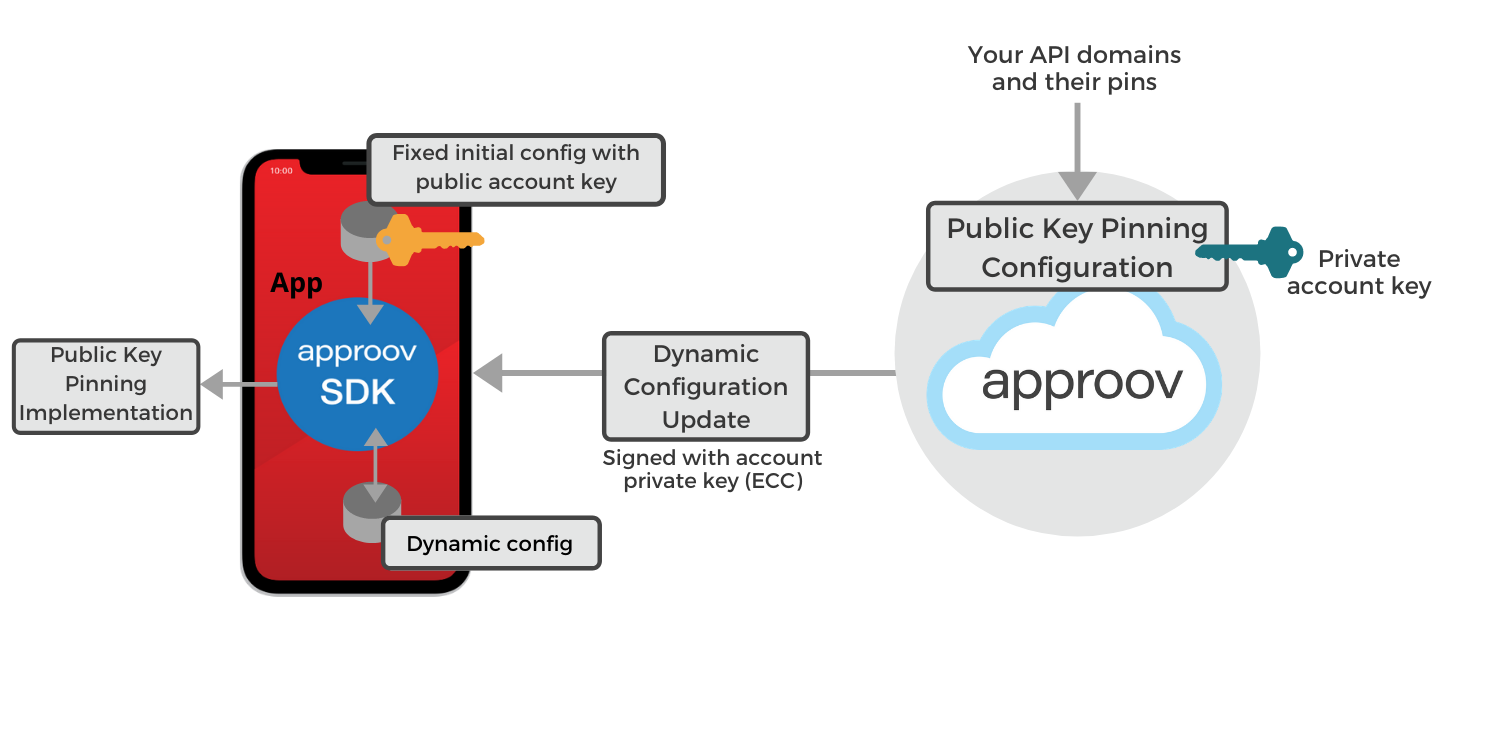
How to Protect Against Certificate Pinning Bypassing
October 15, 2019
Editor's note: This post was originally published in October 2019 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in November 2021. In my previous article, we saw how to bypass certificate pinning within a device you control and in this article we will see how you can protect yourself against such an attack. Read Full Story
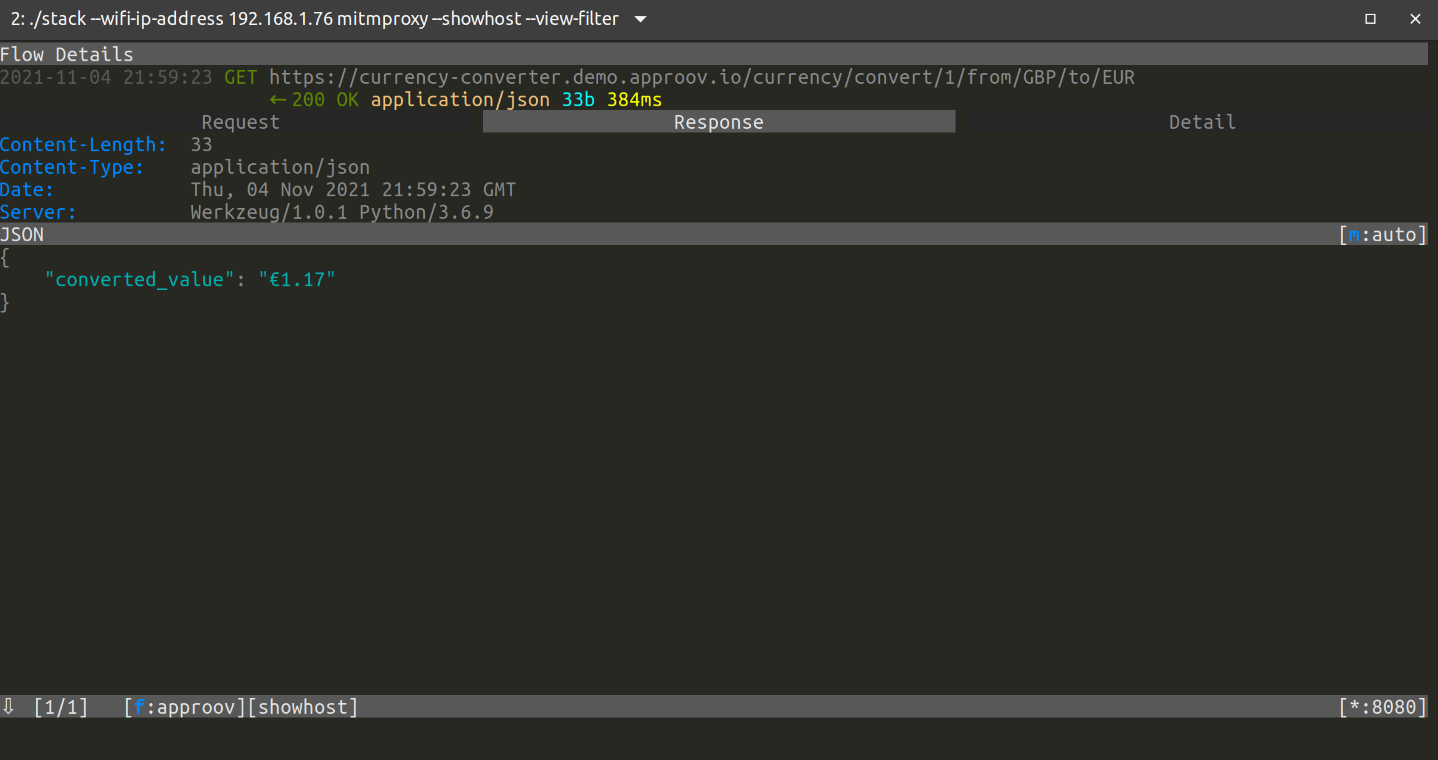
Bypassing Certificate Pinning
August 18, 2019
Editor's note: This post was originally published in August 2019 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in November 2021. In a previous article we saw how to protect the HTTPS communication channel between a mobile app and an API server with certificate pinning, and in this article we will now see how to bypass that certificate pinning. Read Full Story
