
With the implementation of the Digital Markets Act (DMA) in the EU, Apple is opening the possibility of installing apps from alternative apps stores. As discussed in Update on apps distributed in the European Union the intention is that all apps that can be installed must go through a notarization process, which signs the app package with a certificate from Apple. This will be a lighter (and fully automated) review process than will be applied to apps for the official Apple Store.It should prevent the more obvious fake or malicious apps from being installed, but there remains a significant concern that end users will face a wider range of threats should they choose to use third party stores for installation.
Moreover, not only will end users face more threats in the Apple ecosystem, so will app vendors. They will face an elevated risk that their apps will be reverse engineered along with the protocols used to communicate with their backend APIs. API keys that are typically used to secure access to the APIs may be extracted. This allows attackers to build cloned versions of the app, or apps that otherwise unofficially use those APIs, to be published in 3rd party app stores. Such 3rd party app stores may be less responsive to take down requests for such apps where there is an API abuse or other infringement against the original app vendor.
The Increased Importance of App Attestation
We anticipate significantly increased interest in app attestation solutions that ensure that only official apps from the original vendor are able to access backend APIs. While Apple provides the App Attest Service for this purpose, other commercial vendors also provide superior solutions, including Approov.
Vendors should be warned that It is unclear whether the Apple App Attest service will remain available to app vendors even when their app has been published outside of the primary Apple store. Presumably this is possible, however the attestation could simply be measured against the original notarized version of the app.
Given the heightened concern over security in the iOS app marketplace, we expect to see more app developers embracing commercial solutions such as Approov, especially as the coverage is guaranteed regardless of the source of the app store and additionally the burden of integration is much lower than the Apple alternative. Moreover, more attestation options should be provided to app developers operating within the App Store only to make it easier for them to integrate attestation into their existing apps, given the heightened concern over security in the iOS app marketplace.
Approov and Existing App Attest Integration
Approov already provides a highly efficient and robust app attestation solution, operating across Android, HarmonyOS and iOS devices. Our patented solution has been in the marketplace since 2017, based on technologies developed from 2015, when patent filings were first made on the core attestation technology.
The Approov SDK must be included in an app to be attested and this communicates with an attestation cloud service operated by Approov in the AWS and Google Cloud. If the attestation process passes then an industry standard JWT is provided and can be used to authenticate access to backend APIs. Most backend systems include libraries or options to validate JWTs, so that traffic not emanating from valid app instances can be easily blocked at the network edge. Approov has a wide range of backend quickstarts for easy integration:

Source: Approov
Thus integration is considerably easier than for App Attest, where custom token decoding and analysis logic must be integrated into the backend services themselves.
Additionally, Approov has a runtime secrets capability whereby app secrets are only delivered just-in-time to the app if it passes attestation. These secrets can then be used by the app, including as API keys to authenticate access to other APIs. In this case no modification to the backend API is required at all, making integration very fast and straightforward.
The Approov SDK integrates its own mechanisms for determining the authenticity of apps and the environment in which they are running, including various mechanisms to detect if an app is running in a jailbroken environment. App vendors can make fine grain decisions about the characteristics of apps and runtime environments which they will allow.
Approov supports a wide range of frontend quickstarts supporting all popular app development frameworks. These quickstarts, and associated software packages, integrate the SDK with appropriate network interceptors, hooks or other mechanisms to automatically add the Approov JWT or runtime secrets into the API requests being made. Thus the scope of code changes required to integrate Approov remains small and well defined. Attestation authenticity is added to all required network requests without the need for custom logic to determine which particular requests should be protected. Attestation JWTs and runtime secrets are securely cached for a short period to minimize any latency impacts of the attestation process.

Source: Approov
The quickstarts also provide dynamic pinning for connections between the app and the backend API. This prevents any Man-in-the-Middle (MitM) interception or modification of traffic. This isn’t normally possible because of the immutability of the certificate trust store on the device, but can be performed on jailbroken devices where this, or OS code related to it, can be modified. Approov’s pinning provides an additional layer of protection against such exploits.
Approov App Attest Integration
Additionally Approov integrates support for App Attest (and Android’s Play Integrity) so that app vendors can obtain all of the protections afforded by these options in addition to those of Approov.
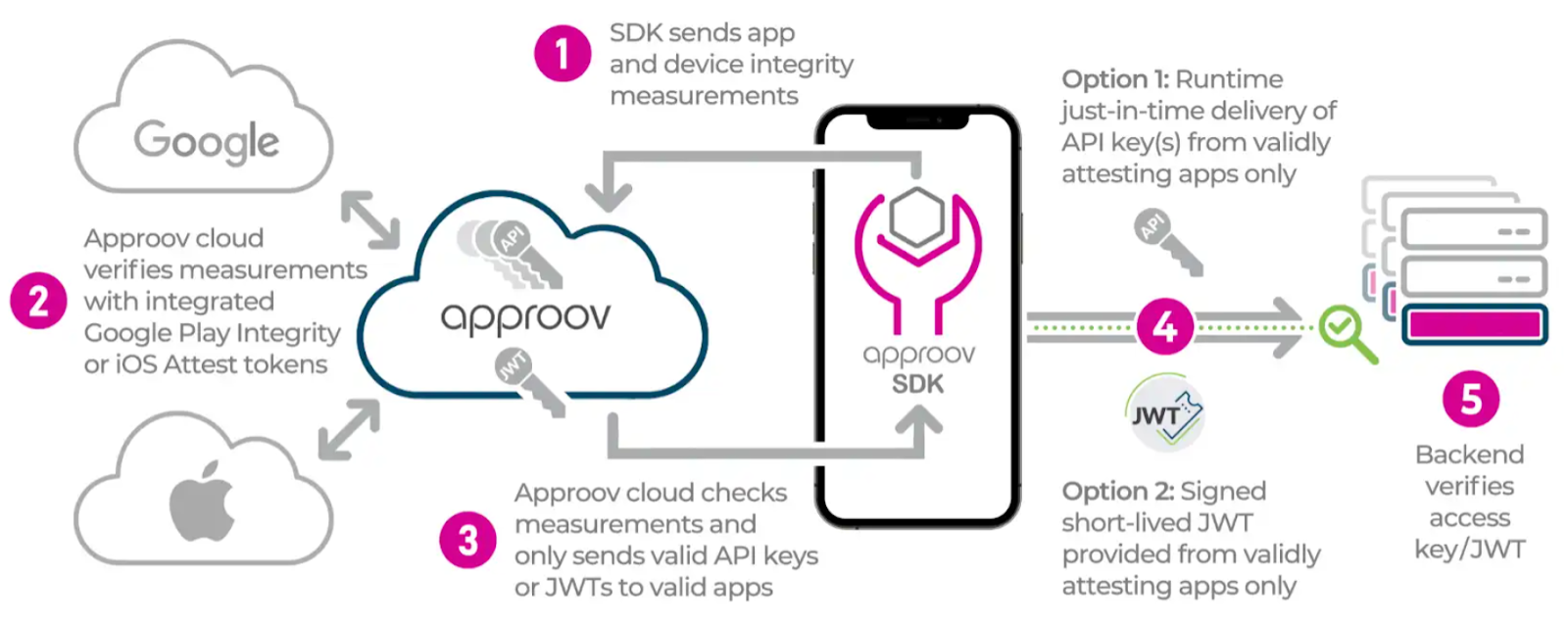
Source: Approov
The step-by-step process is shown in the above diagram. The SDK starts the measurement process on demand, when there is a need to make an external API call that requires proof of app authenticity. The SDK integrates all of the client side logic for performing App Attest, the app vendor only needs to add the required account information to their Approov account as described in Apple App Attest Integration.
Approov handles all of the complexities of the backend App Attest verification process in its cloud service. The App Attest token is passed from the Approov SDK to the Approov cloud without the app developer having to orchestrate this in any way, The Approov cloud can then made a decision about whether the app should be issued with a valid JWT or runtime secrets, based on the results of the App Attest check and the various Approov specific security capabilities. Note that App Attest results may be invalid on jailbroken devices, whereas Approov’s approach provides some additional layers of protection in such cases. Since all of this complex logic is handled in the Approov cloud this obviates the need for the app vendor needing to manage any of this.
Furthermore, the App Attest integration provides attestation on every API call and can automatically initiate a re-assertion of the App Attest keys on a periodic basis. Automatic rate limiting of the use of the App Attest feature across the population of apps, as well as integration with the Fraud lookup capability is also provided.
Conclusion
Approov already provides a comprehensive cross-platform app attestation solution, which is highly optimized for ease of integration into existing apps and backend systems. The DMA requirements on app store access is likely to cause heightened anxiety from app vendors about potential backend API abuse and, with it, an increased demand for app attestation solutions that lock down access to official apps only.


