Approov Blog
Threats (2)

Securing Mobile Gambling Platforms
November 8, 2022
Gambling has come a long way since the days of visiting a bricks and mortar outlet and filling in some paperwork to bet on a small set of events and outcomes. Recent years have seen dramatic changes in this market. In this article we’ll look at how it has evolved and what the security implications are. Read Full Story

Is an API Gateway Secure?
September 14, 2022
An API Gateway is a tool that manages APIs and API traffic. Essentially it sits between remote clients (servers, browsers, mobile apps) and backend services and is responsible for routing API requests in either direction to the right source. But how much security should you expect from an API Gateway? Read Full Story
How is Certificate Pinning Done?
May 17, 2022
Certificate Pinning is a security technique that involves binding a cryptographic certificate to a specific host or domain. This ensures that the app and server communications are protected from man-in-the-middle attacks. Developers can use Certificate Pinning to safeguard against malicious certificates and ensure that only certificates issued by a trusted Certificate Authority (CA) are accepted. When used correctly, Certificate Pinning can be an effective security measure. Read Full Story
What Is In-App Protection?
April 19, 2022
In-app protection refers to the security features built into mobile apps. These features help protect the app and the data it contains from unauthorized access, theft, or tampering. Below, we discuss in-app protection and why it’s crucial for mobile app development. Read Full Story

What is Mobile App Shielding?
April 5, 2022
As mobile devices become increasingly popular in the workplace, so do attacks targeting mobile apps. In fact, according to a recent 2021 cybersecurity study by Checkpoint, 46% of organizations had at least one employee download a malicious mobile application threatening networks and data. What is mobile app shielding and how can it help protect businesses that rely on mobile apps? Read Full Story

Shielding APIs that Service Mobile Apps: Part 4 - When?
March 9, 2022
In the final part of this four part series, we’ll recommend what actions you should take and when you should take them in order to implement effective shielding of your mobile app and APIs it uses. Read Full Story

Shielding APIs that Service Mobile Apps: Part 3 - How?
February 22, 2022
In the third part of this article series, we will look at the component parts of a shielding approach for APIs which service mobile apps and provide some guidance about what to consider when deploying a protective shield around your mobile business. Read Full Story

Shielding APIs that Service Mobile Apps: Part 2 - What?
February 15, 2022
In the second part of this article series, we are going to explore what shielding of APIs connected to mobile apps actually means. To provide some context, we will also look at how the bad guys approach attacking the APIs that connect with your mobile apps. Read Full Story

Shielding APIs that Service Mobile Apps: Part 1 - Why?
February 8, 2022
In this series of articles, we are going to explore the why, what, how and when of shielding APIs that service mobile apps. Increasingly, mobile represents a special case when it comes to security and we will make the case for some explicit steps you should take if you are working within a company that relies on mobile apps to conduct its business. Read Full Story
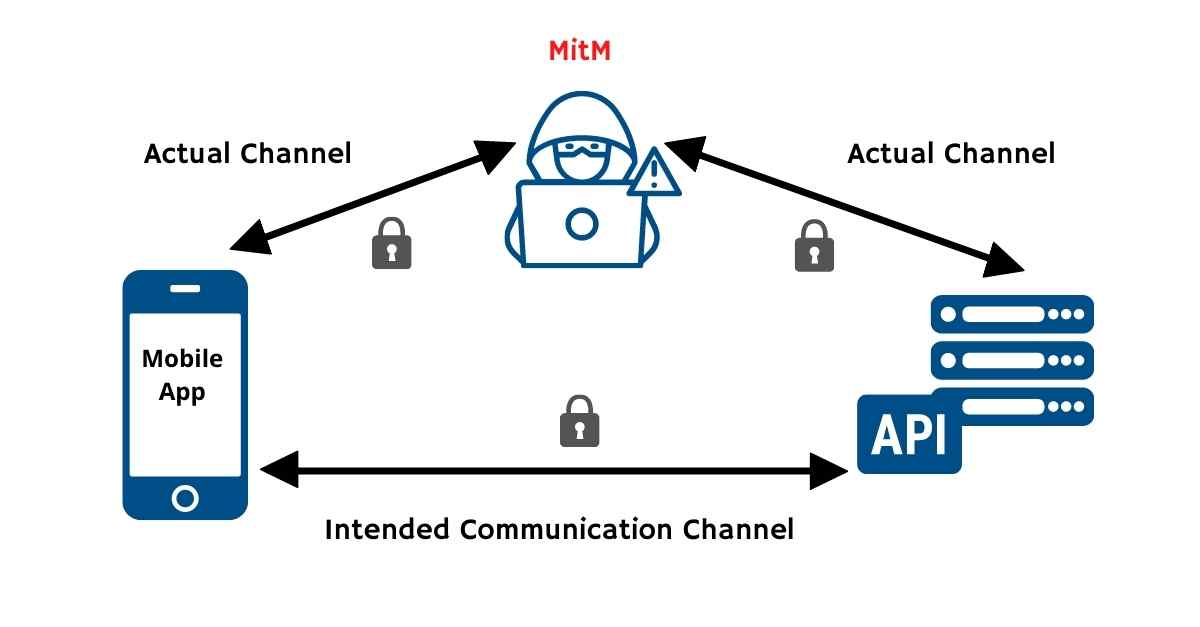
How Certificate Pinning Helps Thwart Mobile MitM Attacks
November 9, 2021
Editor's note: This post was originally published in November 2021 in Cyber Defense Magazine. The massive deployment of mobile apps is presenting new attack surfaces to bad actors and the API channel between the apps and backend services is one of the 5 defined attack surfaces in the ecosystem. In this article we will explore the challenges of defending this channel and outline some practical steps you can take to put immediate protection in place. Read Full Story
