Approov Blog
MitM Attack (4)

Security Key to mHealth Success
July 23, 2020
In 2016, mHealth apps were the third fastest-growing category of apps behind games and utilities. In 2017, the number of healthcare applications available for smartphone users doubled from that of 2015 to 325,000, from 84,000 different publishers, with an estimated 3.7 billion downloads that year. By 2018, nearly a third of all patients were using their mobile phone for health-related searches and for booking appointments, an overwhelming 99% of consumers believed that mHealth apps improved their quality of life and 70% of millennials were interested in a mobile app that would help them actively manage their well-being. By 2027, mHealth app usage among patients is projected to grow at a 10-year CAGR of 40%. Read Full Story

Preventing Faked Proximity
May 15, 2020
We’ve been thinking a lot about contact tracing apps in recent weeks. There are ongoing debates about whether a centralised or decentralised model is superior, and how the ensuing discussions around privacy will impact their takeup. Read Full Story

Quick Analysis: NHSX Contact Tracing App
May 11, 2020
When the NHSX contact tracing app was made available in the app stores last Thursday we decided to take a quick look at its operation and how the code has been put together. We used the Android version and the excellent MobSF tools to do our reversing analysis. On Friday the full source code of the app was also published on github. Read Full Story

Approov Backend Quickstarts
April 29, 2020
Photo by Ankush Rathi from Pexels Editor's note: This post was originally published in April 2020 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in September 2020. Approov lets your mobile app prove to a backend API that it really is the official mobile app making the call, and that it is not running in an environment that may be compromised. Only requests from the apps that you specifically allow can make successful requests. Read Full Story

Securing the Enterprise for Remote Work
April 2, 2020
At a time when the world could use some good news, any good news, the central health crisis continues to get compounded by a persistent wave of cyberattacks targeted at companies and their employees. Not even healthcare institutions and agencies at the center of responding to the emergency have been spared, with the World Health Organization, the U.S. Department of Health and Human Services and even a UK-based coronavirus testing facility being targeted by cyber profiteers. Read Full Story

Top 5 Threats to APIs Servicing Mobile Apps
March 29, 2020
As mobile apps become increasingly paramount to operating successfully in today’s markets, a big question mark over API security is raised. Gartner has previously predicted that by 2022, “API abuses will be the most-frequent attack vector resulting in data breaches for enterprise web applications.” Since every mobile app out there is powered by APIs, securing them is clearly a top priority. Read Full Story

Blockchain renders online votes immutable, including fake votes!
March 19, 2020
“It's the wave of the future,” declared the US State of West Virginia's Secretary of State of following a limited deployment of a blockchain-based voting app for the state's general midterm elections. For cybersecurity and election integrity advocates, however, the move was “an example of all the things states shouldn’t do when it comes to securing their elections.” Read Full Story
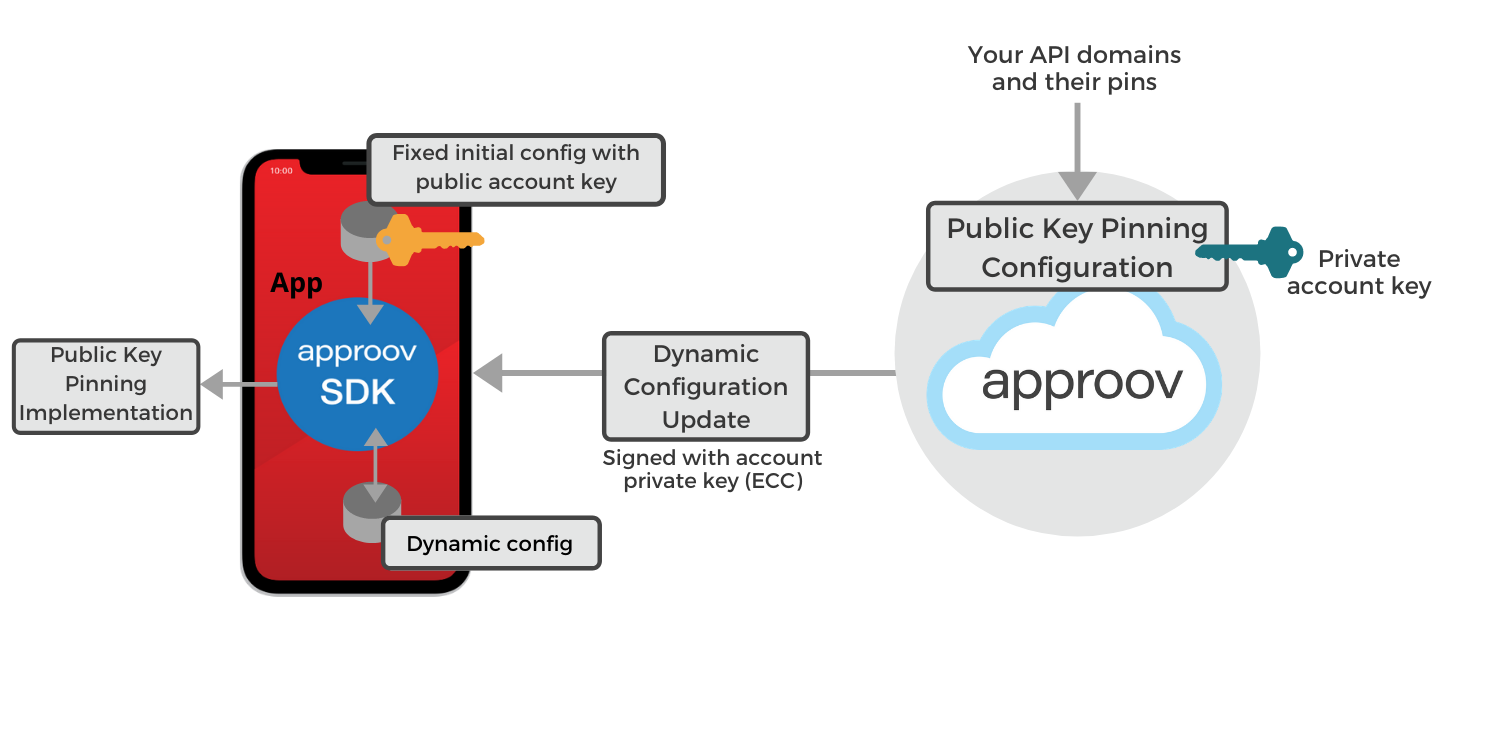
How to Protect Against Certificate Pinning Bypassing
October 15, 2019
Editor's note: This post was originally published in October 2019 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in November 2021. In my previous article, we saw how to bypass certificate pinning within a device you control and in this article we will see how you can protect yourself against such an attack. Read Full Story
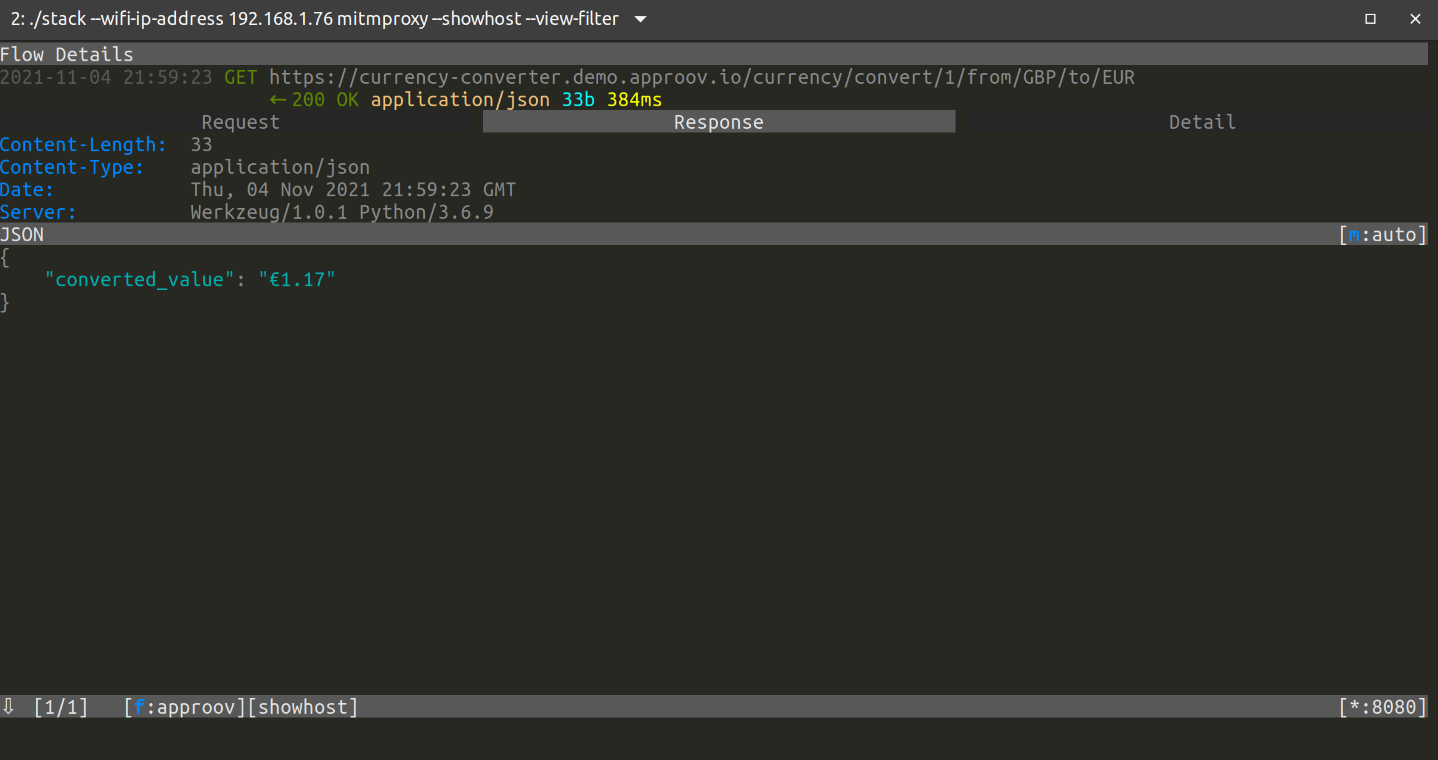
Bypassing Certificate Pinning
August 18, 2019
Editor's note: This post was originally published in August 2019 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in November 2021. In a previous article we saw how to protect the HTTPS communication channel between a mobile app and an API server with certificate pinning, and in this article we will now see how to bypass that certificate pinning. Read Full Story

