Approov Blog
Integration (5)

Practical API Security Walkthrough — Part 4
January 18, 2018
Editor's note: This post was originally published in January 2018 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in May 2021. Welcome back! This is the fourth and final part of a mini series which uses a fictional product, “ShipFast”, to walk you through the process of defending against various exploits in a mobile application to gain access to data on a remote server allowing real users of the system to gain an unfair business advantage at the expense of the company. In this post, I'll dive into the third API security attack scenario and what is required to effectively defend against it. Read Full Story
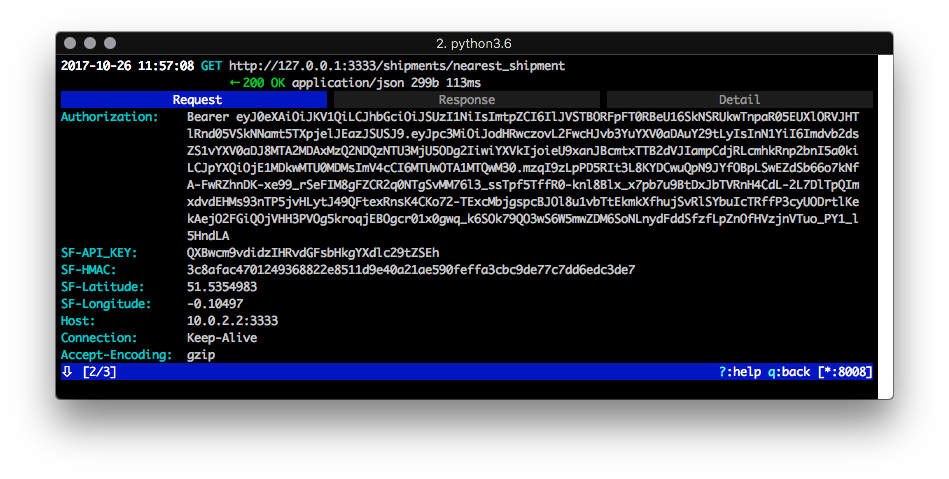
Practical API Security Walkthrough — Part 3
January 17, 2018
Editor's note: This post was originally published in January 2018 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in September 2020. Welcome back! This is the third part of a mini series which uses a fictional product, “ShipFast”, to walk you through the process of defending against various exploits in a mobile application to gain access to data on a remote server allowing real users of the system to gain an unfair business advantage at the expense of the company. Read Full Story
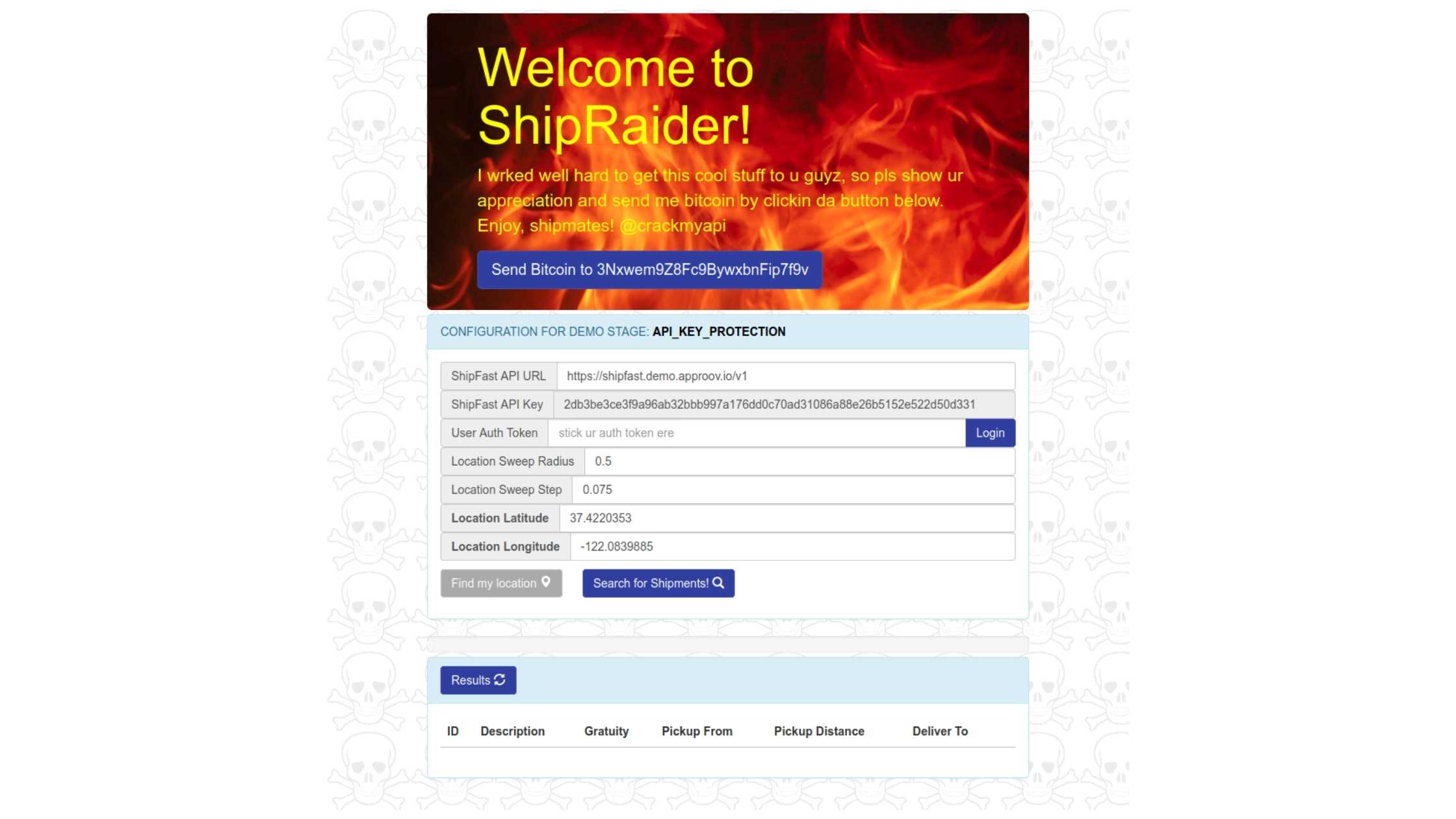
Practical API Security Walkthrough — Part 2
January 16, 2018
Editor's note: This post was originally published in January 2018 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in May 2021. Welcome back! This is the second part of a mini series which uses a fictional product, “ShipFast”, to walk you through the process of defending against various API security exploits in a mobile application to gain access to data on a remote server allowing real users of the system to gain an unfair business advantage at the expense of the company. Read Full Story

Practical API Security Walkthrough — Part 1
January 12, 2018
Editor's note: This post was originally published in January 2018 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in September 2020. Welcome! A quick question: Do you know what’s using your API? Really? Read Full Story

Checking Approov Tokens in ASP.Net Core 2.0
January 10, 2018
We’ve had some requests recently from customers for some examples to show how to use Approov tokens with an ASP.Net Core 2.0 back end. In this blog I’ll walk you through adding the check to a basic API. It’s really straight forward! Thanks to Jon Hilton for this great blog which formed the basis for this example. Read Full Story

Toughen Up Soft Certificate Pinning With Approov
December 14, 2017
Devops just mailed to say they will rotate the certificates on all of the endpoints today, mentioned the Engineering Manager at one of our customers, that’s unexpected, I wonder what happened. Read Full Story
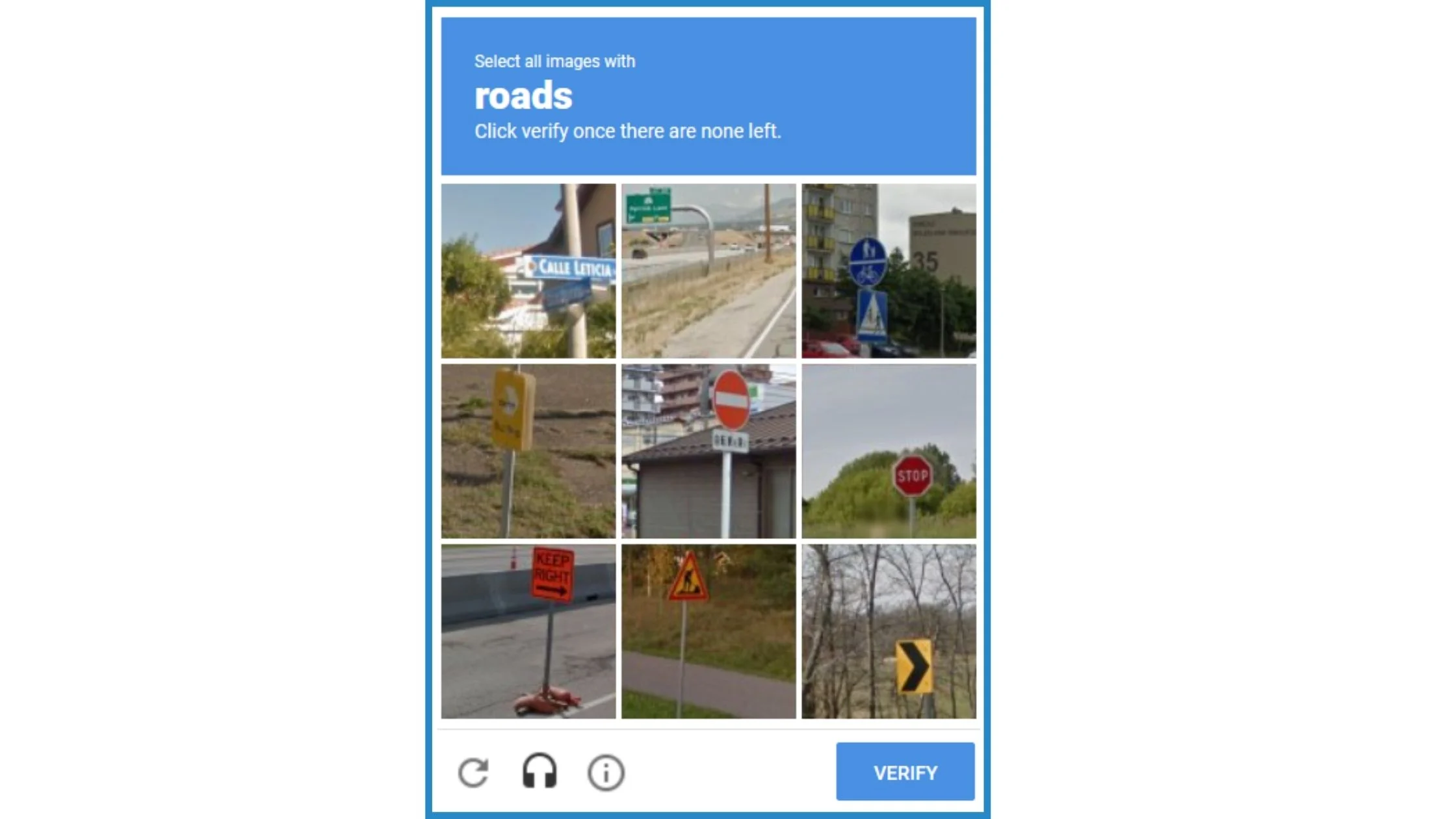
Are You Human, Robot or Just Impatient?
November 28, 2017
Recently I was doing some API analysis on a video sharing app aimed at the teenage market. As is typical in these types of apps, before you can do anything you need to sign up with an account. You’d think that would be straightforward enough, right? Read Full Story

Unintentional Unpinning with Firebase
August 28, 2017
Google's Firebase provides comprehensive set of analytics services for developers to integrate with their apps. On Android the basic functionality is enabled simply by integrating the desired plugins. No code changes required. Read Full Story
The Problem with Pinning
July 13, 2017
Certificate or Public Key Pinning is an extension to TLS that is highly effective for bot mitigation by protecting the HTTPS connection between your app and API from snooping by third parties (otherwise known as a Man in the Middle attack). The technique makes use of the TLS protocol which requires the server to provide a certificate containing its public key. If the client has a copy of the expected certificate (or just the public key) and checks for a match before completing the TLS handshake then the client is considered pinned to the server. Read Full Story
Help Your Mobile API Ecosystem to Flourish
July 5, 2017
(Image via http://maxpixel.freegreatpicture.com) The API for a service faces conflicting demands in order to deliver value to end users. It needs to be open to allow innovation by 3rd party app developers. This is necessary to meet niche customer needs and open new markets for your service beyond what an in house app development team could provide. Read Full Story
