Approov Blog
Integration (4)
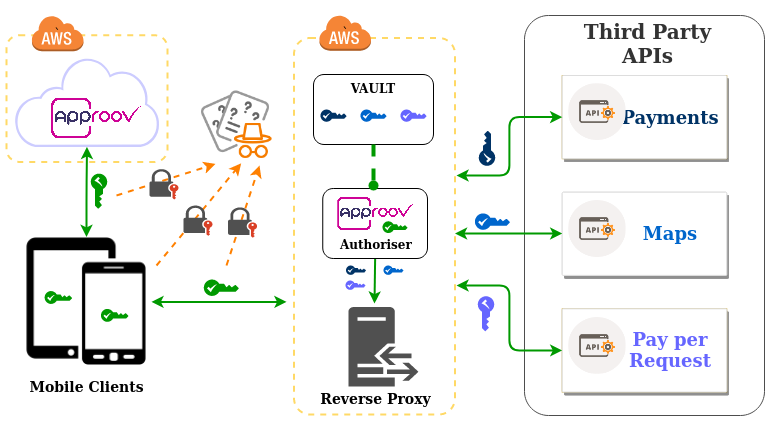
Approov Serverless Reverse Proxy in the AWS API Gateway
February 27, 2020
In my previous article, Using a Reverse Proxy to Protect Third Party APIs, I left you without a solution to secure the purple API key inside the mobile devices in the graphic above from being extracted by the bad guy wearing the orange hat. As promised I am going to show you in this article how you can implement a solution for it. Rather than securing the purple API key, wouldn’t it be better not to have it in the first place or at least to make sure that if it is extracted then it can’t be used at scale by malicious actors? Well that's what a Mobile App Attestation solution is for, and we will start this article by explaining what it is. Spoiler alert: it allows you to secure your API without needing to ship any type of secret inside your mobile app or, if you already have a secret in your mobile app, it allows you to ensure that the secret can’t be used to abuse your API. Read Full Story

Securing Your API server with Approov and Cloudflare
November 19, 2019
Cloudflare is famous among developers as a leading CDN to efficiently deliver customer facing Internet content for their applications, but Cloudflare can also be used to verify all incoming requests before they reach your API server, by leveraging Cloudflare workers. Read Full Story
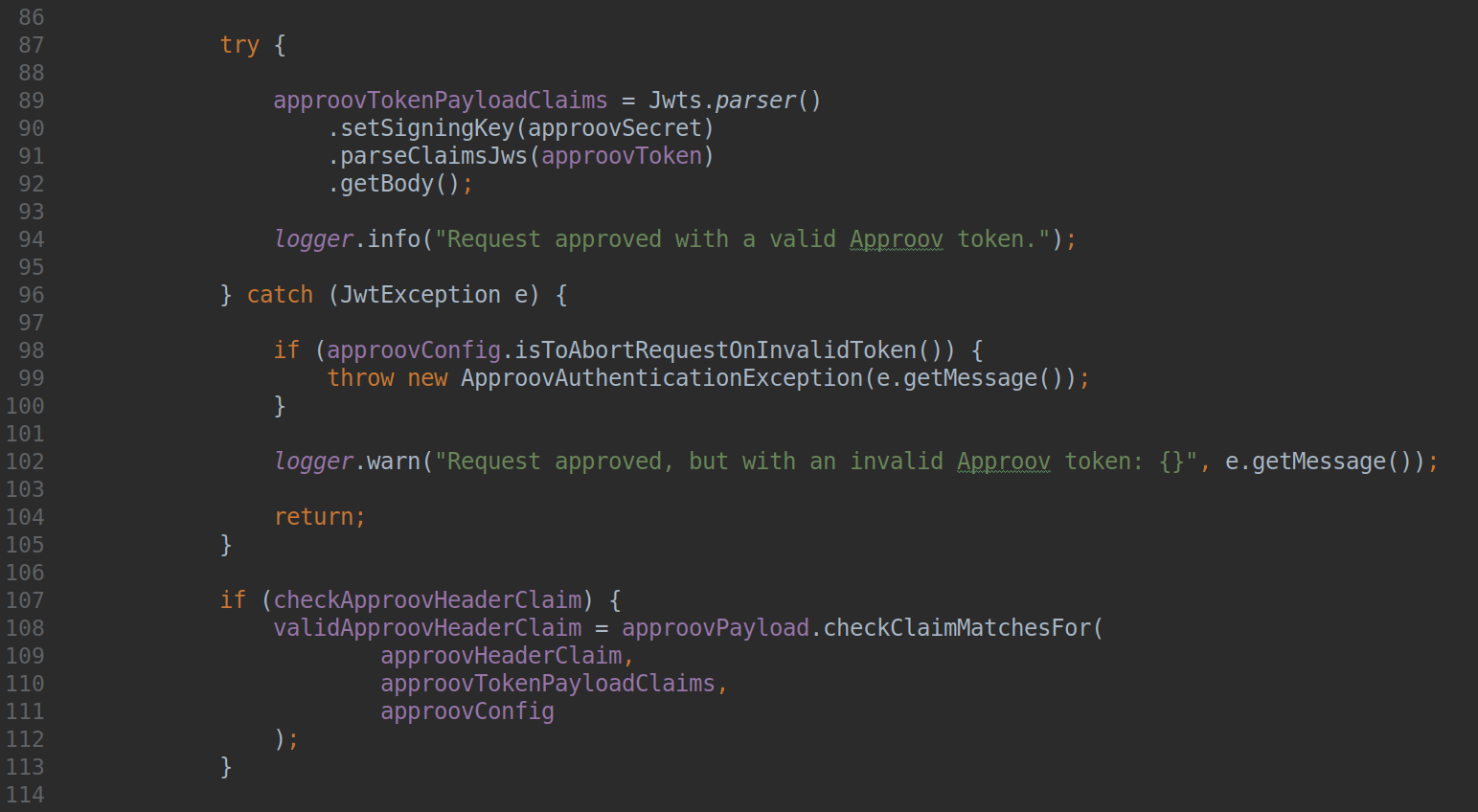
Approov Integration in a Java Spring Stateless API
May 9, 2019
This walk-through will show how simple it is to integrate Approov in a stateless API server using Java and the Spring framework. We will see the requirements, dependencies and a step by step walk-through of the code necessary to implement Approov in a Java Spring stateless API. Read Full Story
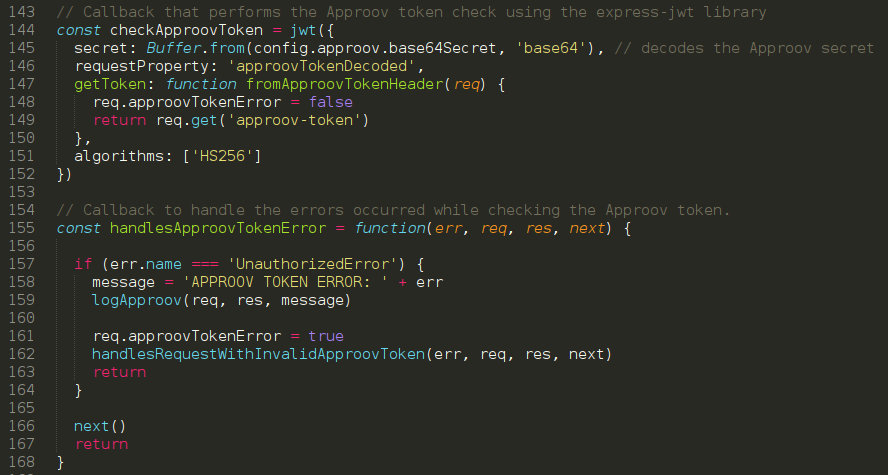
Approov Integration in a NodeJS Express API
February 5, 2019
This walk-though will show us how simple it is to integrate Approov in a current API server using NodeJS and the Express framework. We will see the requirements, dependencies and a step by step walk-through of the code necessary to implement Approov in a NodeJS Express API. Read Full Story
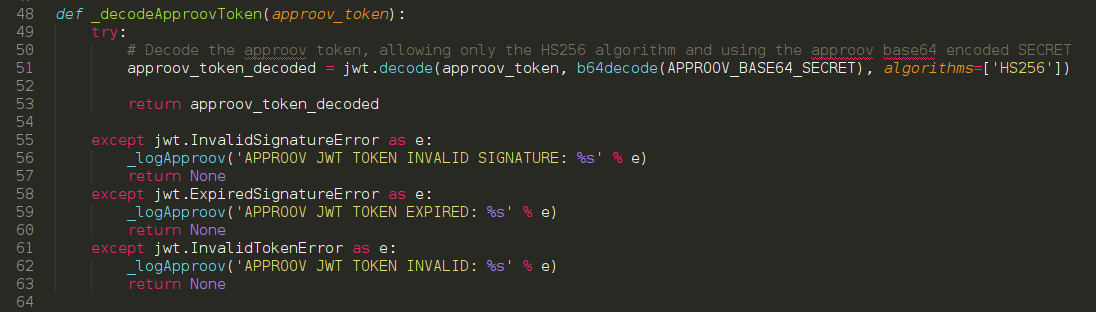
Approov Integration in a Python Flask API
February 4, 2019
This walk-though will show us how simple it is to integrate Approov in a current API server using Python and the Flask framework. We will see the requirements, dependencies and a step by step walk-through over the code necessary to implement Approov in a Python Flask API. Before we tackle the integration of Approov we need first to know how Approov validation is processed in the server and how to setup the environment to follow this walk-through. Note that this article assumes a basic understanding of the Approov mechanics. If you need an overview of that, please read first the Approov Product page. Read Full Story

42Crunch and CriticalBlue Announce Partnership
November 23, 2018
Joint solution to ensure APIs are built correctly and used legitimately. Read Full Story

Approov Cordova QuickStart
June 15, 2018
Editor's note: This post was originally published in June 2018 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in July 2020. Our aim is to make the process of integrating Approov into your mobile app easy. Our Cordova Advanced-HTTP Quickstart allows you to get up and running with Approov easily, whether you are building a new Cordova app that uses Cordova Advanced HTTP or are adapting an existing one to have an improved security posture. Read Full Story


A Tour of API Underprotection
April 3, 2018
An OWASP AppSec California 2018 Talk The fifth annual OWASP AppSec California was held in late January 2018 on the beach in Santa Monica. AppSec California is organized and run by an all-volunteer staff, and they put on a great conference — highly recommended. Besides excellent content and a chance to interact with many interesting colleagues, who wouldn’t want to hang out on the beach for a few days? Read Full Story

What if I Want to Cancel?
February 1, 2018
Once you've started using Approov, we find it unlikely that you will want to cancel. However, it is a legitimate concern for potential users and, as we have a quick and simple cancellation process, I am happy to address it here. First up, consider the following scenario at the point of cancellation: Read Full Story
