Approov Blog
API Keys (4)
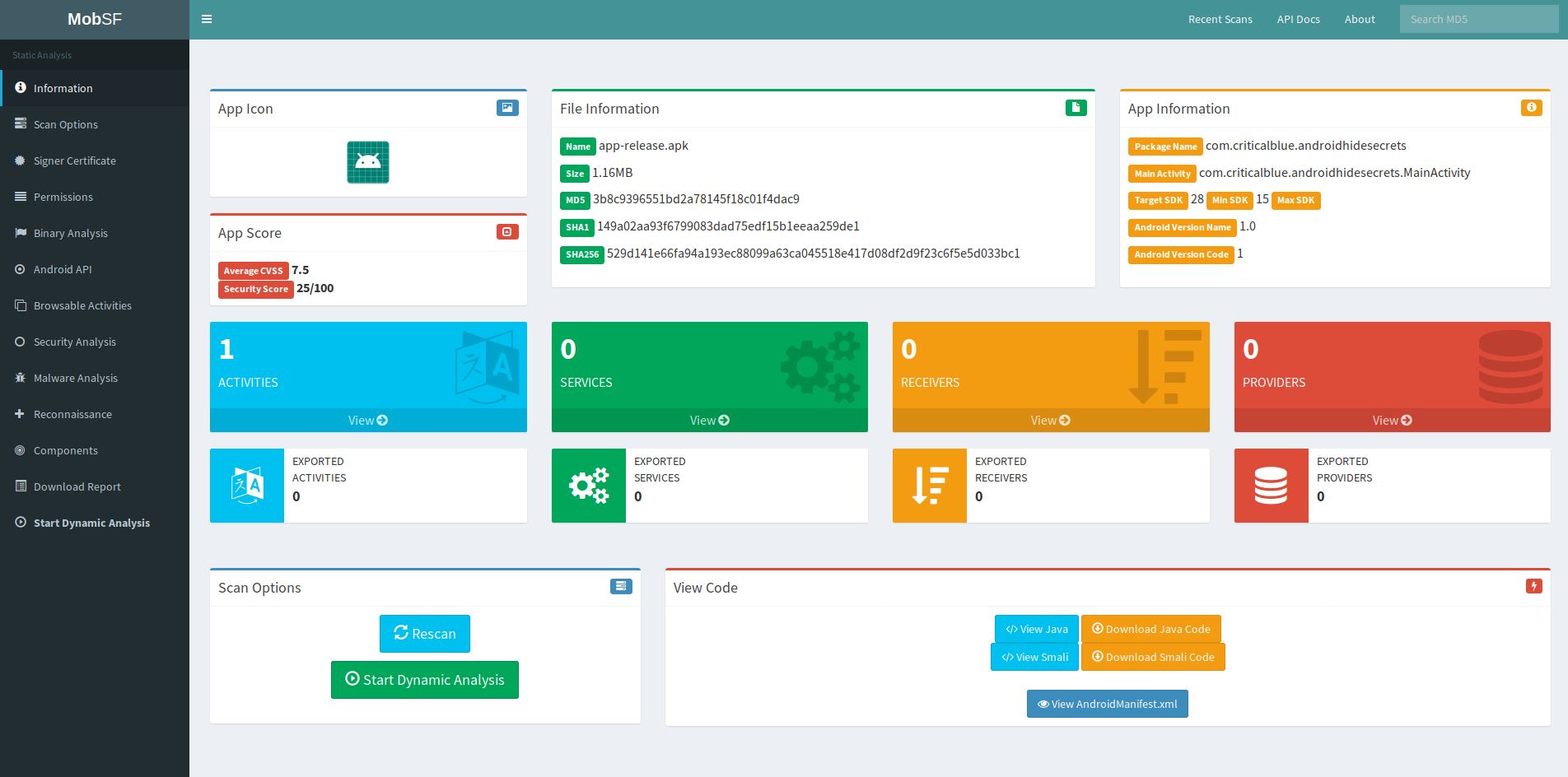
How to Extract an API Key from a Mobile App by Static Binary Analysis
March 14, 2019
An API key is probably the most common method used by developers to identify what is making the request to an API server, but most developers are not aware how trivial it is for a hacker or even a script kiddie to steal and reuse an API key in order to gain unauthorized access to their APIs. In the previous article we saw why your mobile app needs an API key, and now we will see how to grab that API key from your mobile app by reverse engineering the binary in an effective and quick way with an open source tool. Once we see how easy it can be done, we will realize that it is even achievable by non-developers. Read Full Story

Why Does Your Mobile App Need an API Key?
March 1, 2019
Mobile apps are becoming increasingly important in the strategy of any company. As a result, companies need to release new application versions at a fast pace, and this puts developers under pressure with tight deadlines to complete and release new features very quickly. Read Full Story

The Top 6 Mobile API Protection Techniques - Are They Enough?
December 22, 2018
APIs are a necessary and central part of the strategy of any digital business that wants to stay competitive and monetize its assets. Additionally, end users’ form factor of choice when using digital services is now firmly mobile. The trend towards APIs and mobile devices has moved the attack surface in a significant way and digital businesses must adapt and evolve their security policies accordingly. Read Full Story

Is Your Mobile App Leaking Secrets?
October 30, 2018
In Why Exposed API Keys and Sensitive Data are Growing Cause for Concern, Janet Wagner points out that the exposure of sensitive data through code is a growing cause of concern as developers rely more and more on the cloud for the overall workflow during development and deployment of their applications and in accessing third part services at run-time from within them. Read Full Story

A Tour of API Underprotection
April 3, 2018
An OWASP AppSec California 2018 Talk The fifth annual OWASP AppSec California was held in late January 2018 on the beach in Santa Monica. AppSec California is organized and run by an all-volunteer staff, and they put on a great conference — highly recommended. Besides excellent content and a chance to interact with many interesting colleagues, who wouldn’t want to hang out on the beach for a few days? Read Full Story

A Brief Introduction to Approov
January 19, 2018
An article on wired summarises 25 data breaches that made headlines during 2017. The implication in the article, and the general impression of those who take an interest, is that 2018 will bring more of the same in an ever accelerating trend of discovery and disclosure. The growth in attacks indicates that companies of all sizes should continually raise the defensive bar and Approov raises that bar significantly. In this short post I will provide a high-level view of what Approov does and how it works. Read Full Story

Whitelists & Indirection Go Together Like Chocolate and Peanut Butter
July 28, 2017
source: nourishmorelove Used properly, whitelisting is a simple and effective security tactic to minimize attack surfaces. If you’re not on the list, you don‘t get in. No exceptions. Smooth as chocolate. If it’s too easy for you to find and spoof a name on the list, use indirection to make it harder. Sticky as peanut butter. Together they taste great. Read Full Story
Help Your Mobile API Ecosystem to Flourish
July 5, 2017
(Image via http://maxpixel.freegreatpicture.com) The API for a service faces conflicting demands in order to deliver value to end users. It needs to be open to allow innovation by 3rd party app developers. This is necessary to meet niche customer needs and open new markets for your service beyond what an in house app development team could provide. Read Full Story

How Python Coders Killed my Supposedly Secure JavaScript API Service
June 15, 2017
One Developer's Bad Dream Disclaimer: No Python or JavaScript coders were harmed during the writing of this article. All actions involving coders were safely simulated and purely fictional. Read Full Story

Hands on Mobile API Security: Pinning Client Connections
May 31, 2017
Add TLS and Certificate Pinning While Removing Client Secrets The Hands On Mobile API Security: Get Rid of Client Secrets tutorial demonstrates how to improve API security by removing vulnerable API secrets from mobile apps. In the tutorial, you work with a simple photo client which requires an API key to access NASA’s picture of the day service. An API Proxy, introduced between your client and the picture service, removes the need for storing and protecting the API key on the client itself. Read Full Story
