Approov Blog
API Keys (3)

Approov Integration for Elixir Phoenix Guardian Backends
December 2, 2020
The Elixir programming language was created by Jose Valim in 2012 as a research project at Plataformatec, the company where he worked at the time. You can watch Elixir: The Documentary where he tells in the first person more about the motivations and reasons behind writing it. Read Full Story

Approov Integration for Python Django Backends
November 27, 2020
The Python Django framework was created in the last quarter of 2003 by Adrian Holovaty and Simon Willison when they were working as Python developers at the Lawrence Journal-World newspaper, although it was only released in July 2005. Read Full Story

Approov Integration for Python Backends
November 26, 2020
Python is a high-level and general-purpose programming language that is dynamically interpreted at runtime. Python was created by Guido van Rossum in the late 1980s but only released to the public in 1991, as a successor to the ABC programming language. Read Full Story

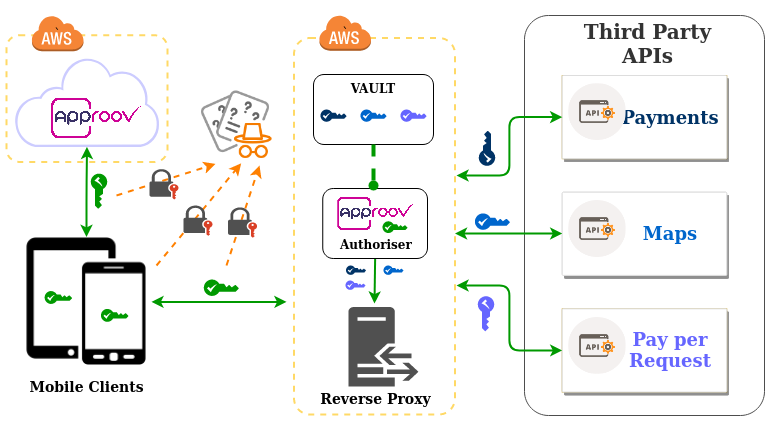
Approov Serverless Reverse Proxy in the AWS API Gateway
February 27, 2020
In my previous article, Using a Reverse Proxy to Protect Third Party APIs, I left you without a solution to secure the purple API key inside the mobile devices in the graphic above from being extracted by the bad guy wearing the orange hat. As promised I am going to show you in this article how you can implement a solution for it. Rather than securing the purple API key, wouldn’t it be better not to have it in the first place or at least to make sure that if it is extracted then it can’t be used at scale by malicious actors? Well that's what a Mobile App Attestation solution is for, and we will start this article by explaining what it is. Spoiler alert: it allows you to secure your API without needing to ship any type of secret inside your mobile app or, if you already have a secret in your mobile app, it allows you to ensure that the secret can’t be used to abuse your API. Read Full Story
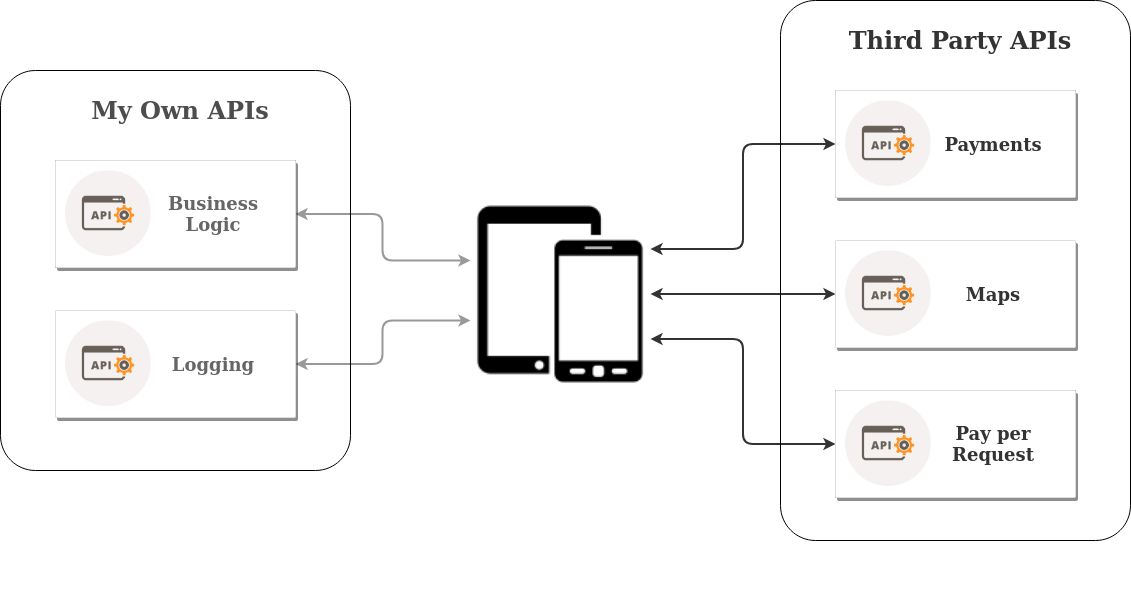
Using a Reverse Proxy to Protect Third Party APIs
February 12, 2020
In this article you will start by learning what Third Party APIs are, and why you shouldn’t access them directly from within your mobile app. Next you will learn what a Reverse Proxy is, followed by when and why you should use it to protect the access to the Third Party APIs used in your mobile app. Read Full Story

Getting Authentication Correct
January 22, 2020
For zero trust mobile apps and APIs, credentials aren’t nearly enough. Read Full Story


Apple DeviceCheck and CriticalBlue Approov
April 27, 2019
We are often asked by customers and prospects to compare our beloved Approov with Apple's DeviceCheck offering. Since DeviceCheck is intended to uniquely identify iOS phone instances then this is a reasonable question. However, DeviceCheck and Approov are designed to do quite different things and therefore we wrote a handy guide to help our customers appreciate when to employ each solution and why. You can download the guide from here. Read Full Story
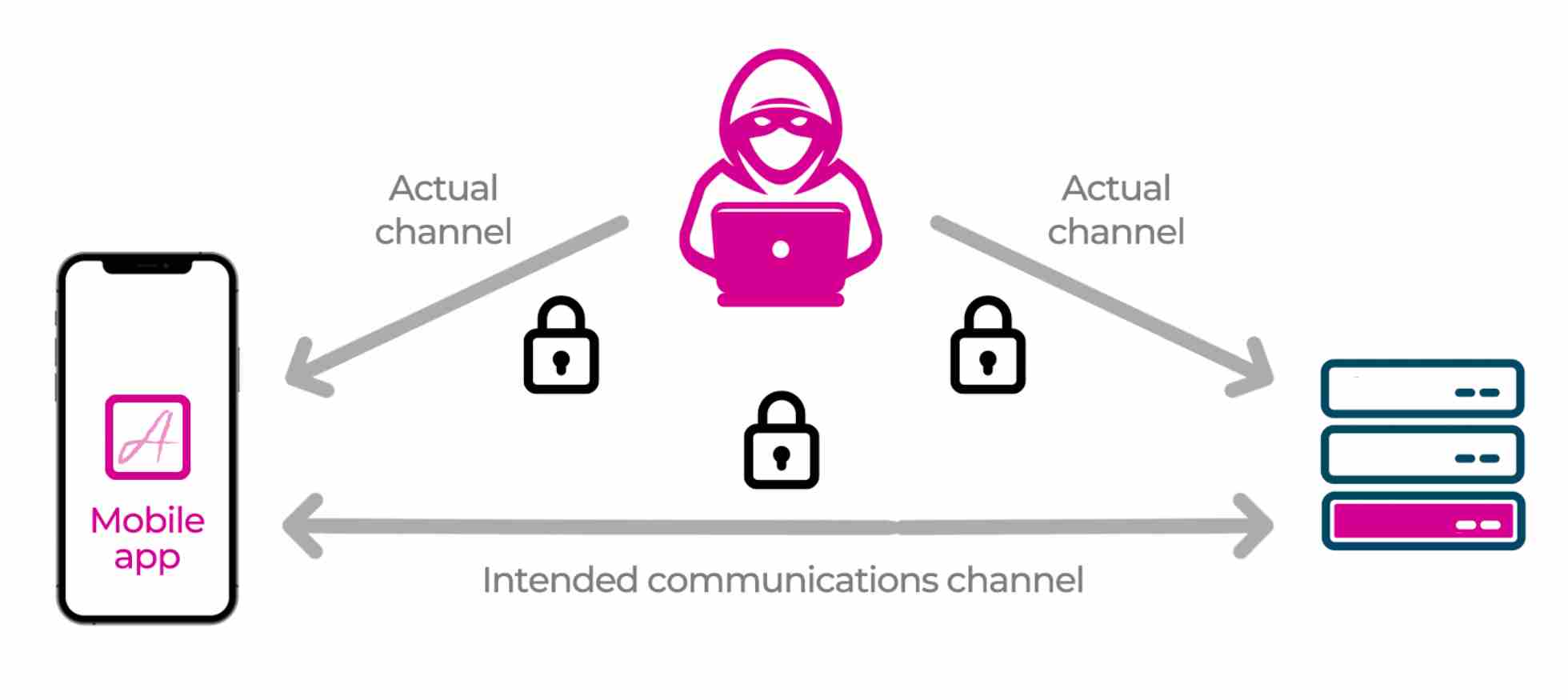
Steal That API Key with a Man in the Middle Attack
April 4, 2019
Editor's note: This post was originally published in April 2019 and has been revamped and updated for accuracy and comprehensiveness. The latest update was in November 2021. As I promised in my previous article, here is the follow up article about performing a man-in-the-middle (MitM) attack to steal an API key, and to follow this article you will need to become the man sitting in the middle of the actual channel, using mitmproxy to help you with the task of stealing the API key. Now it should be clear why MitM stands for man in the middle! Read Full Story
