
This overview outlines the history and use of Apple DeviceCheck including the DeviceCheck App Attest feature. It will highlight how this security solution is used and highlight some limitations. We also compare and contrast Apple DeviceCheck and App Attest with the comprehensive mobile security offered by Approov.
Why App Attestation and Device Integrity Checks are Important
There are two fundamental security challenges with mobile apps: The first is that they can be reverse engineered, even if an obfuscation tool has been used. The second is that they run in a client environment which is open to hackers and is neither owned or controlled by the app owner.
Unless steps are taken, apps can be analyzed, understood, cloned or copied, and the environments they run in can be hacked, rooted, instrumented and manipulated to interfere with the operation of an app.
Using these attack surfaces, hackers can directly intercept or tamper with data transferred between the app and its servers, intercept or manipulate any transactions, or simply interfere with or stop the operation of the service.
Manipulated apps can be repackaged and redistributed with malware. Repackaged apps can be turned into automated tools (i.e. bots) to be used to attack APIs and backend servers. Secrets can also be lifted from apps then used in scripts to create bots.
Bad actors use these techniques to carry out brute-force attacks, exploiting API vulnerabilities to steal data, or mount DDoS attacks on backend servers.
Because of this, taking steps to prevent apps and devices from being tampered with must be at the heart of any security strategy. However, this is only a fraction of the whole story, as we will explain. App and device attestation are an essential piece of the puzzle but not sufficient in themselves.
Different services are available to provide app attestation. Apple provides some app attestation and client integrity functionality in Apple DeviceCheck. Approov provides a unique and patented approach to end-to-end mobile app security, which includes app and device integrity checking. The rest of this paper compares the solutions from Apple and Approov.
The History of DeviceCheck and App Attest
DeviceCheck is an iOS framework, first introduced in iOS 11. The primary use-case for DeviceCheck when it was launched was to provide developers a way to distinguish between customers who have received premium content in an app, and those who have attained it through illegitimate means: basically, developers could set a flag when a customer claims a free offer and use the flag to ensure that they don't claim it twice.
In August 2020, with the release of iOS 14, Apple added a new API to the framework called App Attest. As a part of DeviceCheck, it was intended to help to prevent the inappropriate use of developer servers through compromised apps.
What Problem Do Apple DeviceCheck and App Attest Aim to Address
As we mentioned, DeviceCheck was introduced as a way to stop users claiming special offers more than once. When the App Attest feature was added, Apple noted in developer documentation that apps can be modified and distributed outside of the App Store, leading to versions of those apps with unauthorized features like "game cheats, ad removal, or access to premium content." App Attest was put in place to provide some guarantee that apps are genuine and untampered.
Implementing DeviceCheck and App Attest together allows you to:
Manage the Device State
DeviceCheck Binary flags: You can set and query two binary flags per device using Apple's servers. These flags are like switches you can flip based on your app's needs. It's up to you how you use them. For example, you could:
- Set a flag when a user claims a free offer, preventing them from claiming it again on the same device.
- Flag a device suspected of fraudulent activity for further investigation.
Apple maintains the state of these flags for you, even if the user uninstalls and reinstalls your app. This ensures consistency and prevents abuse.
Verify App Integrity
Using App Attest, your app generates a special cryptographic key on the device and has Apple verify its validity. This helps your server:
- Distinguish your genuine app from pirated or tampered versions.
- Grant access to sensitive resources like premium content or secure transactions with greater confidence. By guaranteeing the app's authenticity, App Attest helps prevent unauthorized access, fraud, and malware outbreaks.
How Does Apple Device Check Work?
DeviceCheck provides developers a reliable way to identify a device and can store two bits of information about the device per app. The flags are maintained even if the app is deleted and reinstalled, a user logs in with different credentials or a system reset is performed. Typical flags can be used to indicate ‘Has this device ever been compromised?’ or ‘Has this app’s free promotion period been used for this device?’.
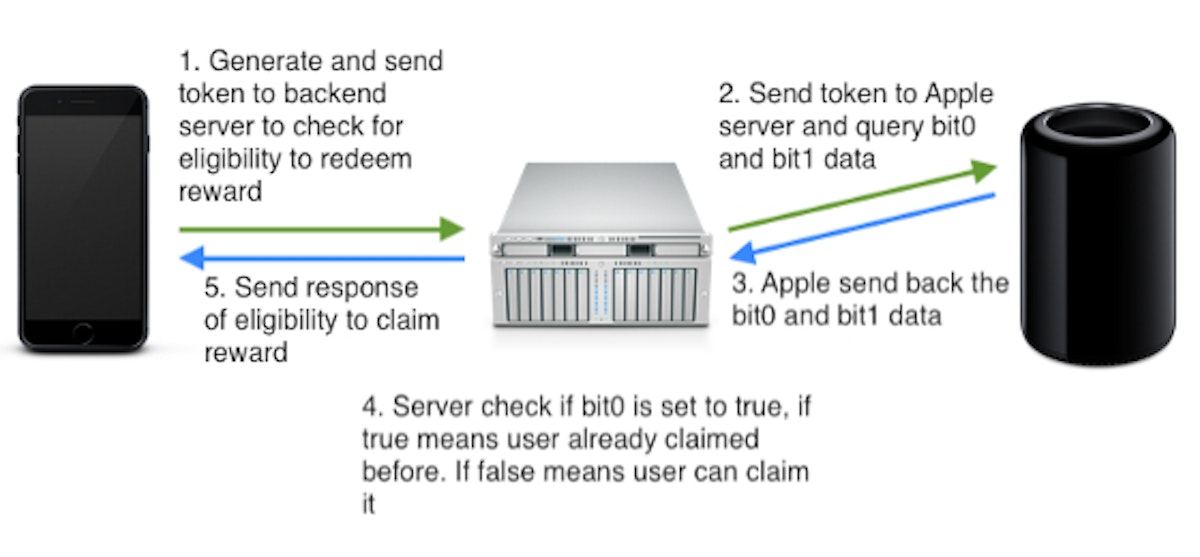
Source: Uniquely identify iOS device using DeviceCheck
The DeviceCheck API generates an ephemeral token which uniquely identifies the device to Apple. Your API service combines this token with an authentication key from Apple and requests or updates the flags identified by the per-device bits and maintains a timestamp indicating when they were last modified.
The DeviceCheck implementation assures users of their privacy even while uniquely identifying the device. Developers receive only an ephemeral token, rather than a device serial number or any other identifying information. Similarly Apple stores the flags and timestamps but has no idea of how the flags are interpreted.
From an app authentication perspective, the flags could be used to identify compromised devices or apps, but it is still up to the developer to determine the app’s authenticity. Since app and device conditions change frequently, the ability to store the last authenticity check is of only marginal value.
How Does Apple App Attest Work?
There are three high-level components involved in App Attest;
- Your iOS application
- The backend server of your application
- the App Attest service
Critically, the App Attest Service is an internet-exposed service, which may fail or timeout from time to time.
In summary this is how it works:
- Your server delivers a string of random bytes which represents a challenge to your app.
- Your app creates a cryptographic key-pair using the Device Check API. The key resides in the device's "Secure Enclave" and the operation responds with a reference to that public/private key pair with an identifier string (the key ID string is a SHA256 hash of the public key).
- A hash of the challenge data along with the key identifier is sent to the Apple App Attest service over the internet. The service responds with the attestation data as a string of bytes.
- The attestation data is provided to your server, and the server validates the attestation data.
- Subsequent requests to your server are then accompanied by assertion data which are generated on the device with the key identifier and the request body.
- The assertion data is then validated and the request is processed.
Step 6 is actually very complicated and merits a 9-step explanation of its own in the Apple documentation. Ultimately, however, it lets you verify that the token you receive comes from your app on an Apple device.
What Problems Do Apple DeviceCheck with App Attest Not Address?
It is obvious DeviceCheck works only for iOS and doesn't help for Android and other client OS or with cross-platform development frameworks. We will talk more about that in the next section.
We will also see in the next section that even if we look only at app attestation alone, there are some shortcomings in the Apple approach.
To be fair, these tools are not intended to provide an “end-to-end” solution. Apple states that DeviceCheck and App Attest contribute to an "overall risk assessment” of your environment and they see it working as part of a bigger effort to secure your mobile apps.
To put things in some context, we can use, for example, the OWASP MASVS (Mobile Application Security Verification Standard) framework which is a comprehensive framework used to assess end-to-end mobile app security.
Apple ONLY partially addresses the guidelines in the category MASVS-RESILIENCE, which is only one of seven categories in the guidelines. MASVS-RESILIENCE aims to ensure that the app is running on a trusted platform, prevent tampering at runtime and ensure the integrity of the app’s intended functionality.
In particular there are two other key things in MASVS that Apple DeviceCheck does not address which you will need to take care of:
- Network and Channel Security: The APIs and the communications channel between app and APIs must also be protected.
- Management and Security of API Keys and Secrets: The secrets used to authenticate and authorize access to backend services from mobile apps must be protected from being stolen and abused. Developers need to manage cryptographic keys securely and handle key rotation appropriately for ongoing security.
Now we understand the overall scope, let's look specifically at the app attestation and device integrity checks provided by Apple and compare them with Approov.
What are the Limitations of Apple DeviceCheck and App Attest versus Approov?
iOS Only
- Obviously the Apple solution only works with Apple iOS devices and does not work with Android or other client/app ecosystems. Implementing diverging security solutions for Android and iOS does not align well with efforts to save development and maintenance costs by using cross-platform development tools such as Flutter and React Native.
- Approov covers all the devices that could be accessing your APIs, including iOS, WatchOS, Android and HarmonyOS. Approov also integrates easily with a number of cross-platform solutions including Flutter and React Native.
And Not All iOS Apps and Devices are Covered
- Not all devices can use the App Attest service, so it’s important to have your app run a compatibility check before accessing the service. If the user’s app doesn’t pass the compatibility check, you are advised to gracefully bypass the service. In addition most app extensions don’t support App Attest. The method to generate a key fails when you call it from an app extension, regardless of the value of isSupported. The only app extensions that support App Attest are watchOS extensions in watchOS 9 or later.
- Approov works even with Jailbroken or manipulated iOS client environments and gives detailed, highly granular visibility of what is going on in the client and equally granular policy enforcement to define what is acceptable or not. It also works on Apple WatchOS.
Potential for Circumvention
- While App Attest can verify an app's authenticity, it doesn't guarantee that it's running on a genuine, unmodified device. Sophisticated attackers could potentially clone a device's identifiers and bypass App Attest or potentially manipulate App Attest results.
- Approov checks an app's authenticity and performs detailed checks on the client environment.
Limited Client Integrity Checks
- App Attest focuses specifically on verifying the integrity of the app itself. It doesn't address other security risks like malware or runtime attacks. It doesn't detect jailbroken devices or runtime app manipulation via hooking or swizzling.
- Approov attests the actual executing code, while Apple attest is restricted to session-based verification. This means Approov provides more robust protection against runtime tampering or compromises like hooking/function swizzling. It also protects against dynamic instrumentation tools and jailbroken devices. Approov provides a rich set of device attestation checks which are regularly updated as new threats emerge. Rooted and jailbroken phones are detected. Frameworks and hooking environments such as Cycript, Cydia, Xposed, Frida, Magisk, Zygisk are all detected. What is acceptable can be controlled with a high level of granularity via over the air policy updates.
Apple Provides Limited Analytics
- The only usage data you can get from App Attest according to Apple is “an approximate count of unique attestations for your app on a particular device. A count that’s higher than expected might be an indication of a compromised device that’s serving multiple compromised instances of your app. You can use this information to assess your risk”. App Attest doesn't provide information about user behavior or device usage patterns, which could be valuable for detecting fraudulent activity or risk assessment.
- Approov analytics on the other hand, shows what is happening in your service, with real-time and historical data. Information is presented via a dashboard presenting a top level view and then allowing deeper investigation via the various graphs and options which are available. This is important not only to measure and report on the effectiveness of the solution but also to help secure and maintain regulatory compliance.
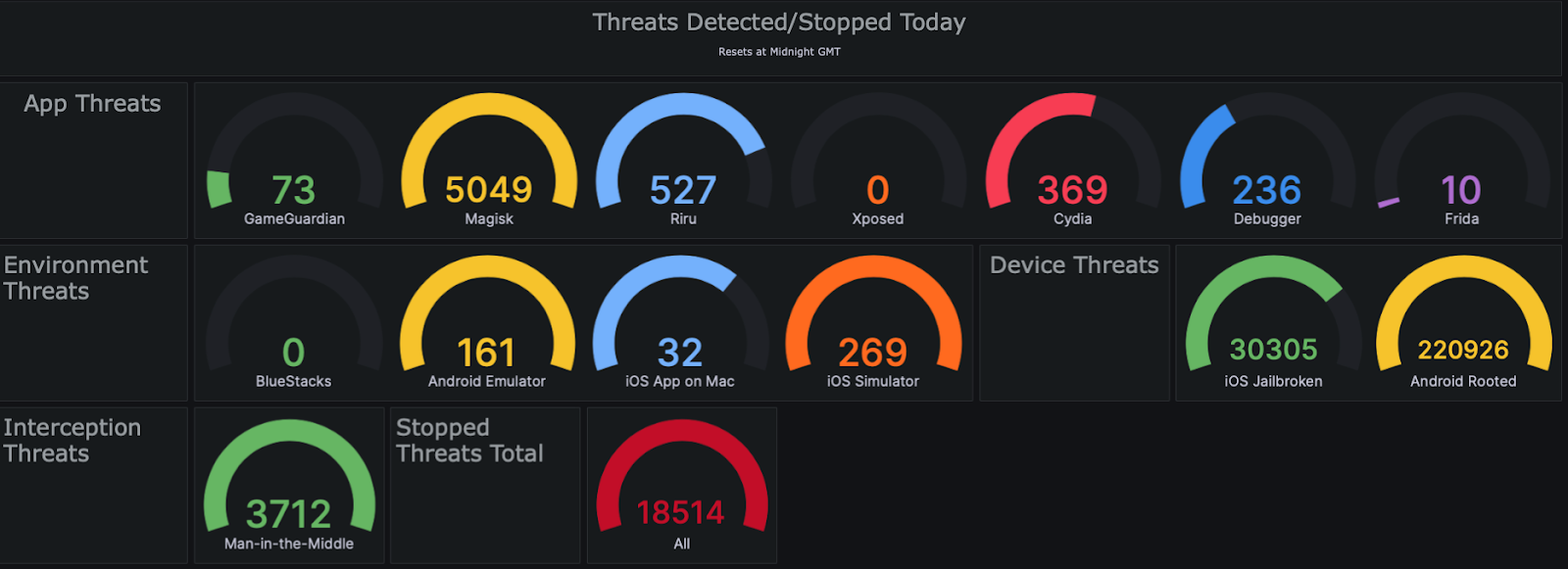
Approov Threat Real-time Threat Reporting. Source: Approov
Implementation Challenges
- Developers have raised concerns about how difficult App Attest is to implement properly and the solution also relies heavily on trusting developers to code more defensively. Each network call needs to be implemented using a complex list of sequential framework functions. The backend validation process is extremely complicated and integrating App Attest requires careful server-side implementation to handle key validation, challenge responses, and risk assessment. Apple documentation lists a 9 step process to determine the integrity of the attestation object at the backend and picking apart the binary data structure which is used is not straightforward.
- Approov makes life easy for developers. Once the SDK is integrated using one of our many quickstarts, app attestation works without any code changes in the app. Approov supports and integrates seamlessly into all modern app development frameworks including Flutter, React-Native, Ionic, as well a native iOS and android. Check out our comprehensive list of quickstarts. The Approov SDK can be tailored to any framework. At the backend, integration is easy also - a simple check of a standard JWT token is required and again there are quickstarts for all major frameworks and environments.
Apple App Attest Does Not Stop API secrets from being stolen and abused
- Apple App Attest can help you distinguish scripts (using stolen secrets) from genuine apps but it does nothing to get secrets out of your app code. It also does not provide any help in keeping your apps running when secrets are compromised, e.g. allowing you to dynamically rotate stolen API keys.
- Approov provides a secrets management solution that manages API keys and certificates securely in the cloud, delivering them “just-in-time” only when app and device integrity checks are passed. It also allows them to be easily rotated via over-the-air updates if they are compromised elsewhere. It also works for third party APIs.
Apple App Attest doesn't prevent Man-in-the-Middle (MitM) attacks
- Mobile phones are particularly prone to Man-in-the-Middle attacks on the channel between the app and the API, even if the traffic is encrypted. App Attest, when it is working, does ensure the attestation data is not modified in transit, but as we have indicated App Attest doesn't work with jailbroken phones or detect runtime app manipulation which are the paths attackers take to intercept traffic.
- Approov Dynamic Certificate Pinning protects the channel from mobile Man-in-the-Middle attacks and makes it easy to manage and rotate certificates over the air.
Performance and Rate Limits
- Apple may throttle App Attest requests to prevent server overload, which could impact app functionality during high usage periods. Apple enforces a rate limit to the number of unique devices calling App Attest at any given moment, and much to the frustration of many app vendors the actual quota is not publicly available. In addition to this, once the quota is met, Apple offers you no SLA to increase it, which makes it very difficult to scale securely.
- Approov has no quotas or thresholds on traffic and can easily scale to support millions of active mobile apps, always providing a consistently high performance. Allowing you to seamlessly and securely scale your apps is at the core of Approov, we’ll provide you with a competitive SLA to suit your business, and you’ll never get charged for attacks, including DDOS mitigation. See our pricing guidelines for more information.
If however, you have already made the effort to understand and implement Apple DeviceCheck/App Attest, it is easy to integrate the attestation information provided by these tools into Approov as part of a defense-in-depth approach. For example DeviceCheck can tell if there is a continual re-installation of an app on the same physical iOS device and App Attest can provide some additional protection against spoofing attempts. In both cases, Approov makes integration easy, taking care of the complexity of Apple integration at the backend. Approov can also mitigate the performance impact of using the Apple tools.
Summary
Apple DeviceCheck and App Attest provide a way to perform app and device attestation checks at runtime. These have some limitations and only work with certain types of iOS apps on unmodified iOS devices.
Approov Mobile App Protection ensures that all mobile API traffic does indeed come from a genuine and untampered mobile app, running in a safe environment. Doing this blocks all scripts, bots and modified or repackaged mobile apps from abusing an API. Approov supports any apps running on Android, iOS, WatchOS and HarmonyOS, providing comprehensive and powerful security with easy and consistent management across all supported platforms.
Subscribe to our monthly newsletter to get all the latest news in mobile security.
Follow us on Linkedin to receive a weekly update.
Image credit: Photo by James Yarema on Unsplash
