
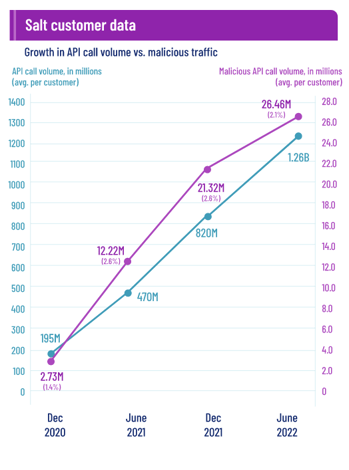
API abuse is a growing concern in today's digital landscape, with criminals finding new and innovative ways to exploit APIs for their own gain. According to a recent study by Salt Security, "malicious API attack traffic surged 117% over the past year, from an average of 12.22 million malicious calls per month to an average of 26.46 million calls." This article explores the topic as it relates to mobile centric businesses.
(Image source: salt.security)
API abuse can take many forms and is the mechanism behind many attack vectors, such as account takeover, fake account creation, denial of service, credit fraud, app impersonation, Man-in-the-Middle attacks, data breaches, and data scraping. Any of these threats can pose a serious risk to your app and its users.
Fortunately, for mobile first and mobile centric businesses, there are several strategies you can use to help protect your API from these attacks and ensure that the valuable data it contains remains secure.
1) App Integrity
The first line of defense against API abuse is to ensure that only genuine, untampered versions of your app can make API calls. This can be accomplished using mobile app attesation, which verifies the authenticity of your app - protecting you against attacks from modified (tampered) apps and scripts which are impersonating genuine apps.
2) Device Integrity
Another way to protect your APIs is to verify the integrity of the devices that are making requests. As a first step this involves checking for a rooted or jailbroken device, which indicates that the device's OS level security has been compromised. You should go further than that because evidence of root or jailbreak is not evidence of a hacker in and of itself. Other checks must be carried out to correctly identify compromised devices, for example detection of debuggers, emulators, simulators, Frida, Magisk, Xposed and cloner apps.
3) Channel Integrity
The communication channel between your app and your backend services should be secure to prevent Man-in-the-Middle attacks. SSL/TLS encryption should be used for all data in transit, and you should verify the identity of the server using a trusted certificate authority. Employing dynamic pinning makes certificate management significantly easier.
4) Credential Integrity
Any credentials used to authenticate with your backend services (such as username/password, OAuth tokens, etc.) should be stored securely on the device and protected from unauthorized access. Additionally, access tokens such as API keys should be protected from abuse by ensuring that a second independently factor is presented to the API endpoint alongside the API key itself. For third party API keys, just-in-time delivery mechanisms can be deployed to ensure that the API keys cannot be abused.
5) Service Integrity
Finally, you should protect your backend services from attack by implementing measures such as firewalls, intrusion detection/prevention systems, and proper access control measures (such as least privilege). You should also consider using a web application firewall (WAF) to protect against common web attacks such as SQL injection and cross-site scripting (XSS).
How Approov Helps Prevent API Abuse
By taking these steps to prevent API abuse, you can help protect your mobile app from attack and keep your revenue safe. Approov provides an additional layer of protection by ensuring that only genuine versions of your app can make API calls, preventing malicious scripts and tampered apps from accessing your backend resources. Approov implements many of the recommendations discussed above. To learn more about how Approov can help protect your mobile app, sign up for a free trial today.